Think of social engineering, in the context of information security, and you probably conjure up an image of Nigerian scammers promising millions in return for bank account details plus a small transaction fee. You probably don’t think that it might involve the “virtual kidnap” of a loved one.
Michael Levin, formerly deputy director of the National Cybersecurity Division of the US Department of Homeland Security and now chief executive at the Center for Information Security Awareness, recounts how the threat works.
Making full use of intelligence from social networks, as well as the malware compromise of mobile devices, attackers stage a fake kidnapping. A call, possibly spoofed to look like it’s coming from the victim’s phone, informs you of the hostage-taking and ransom demand. You may hear what could be your partner sobbing or screaming in the background.
This is social engineering at its most evil; the devil literally being in the detail. By hacking into your computer, your phone and your social networks, they know enough to make the threat very convincing indeed. By compromising a smartphone and having access to the GPS location information, the cybercrooks can even convince the victim that they are watching them.
Panic is induced and ransoms are paid. Earlier this year, the FBI arrested one woman allegedly involved in such scams, involving $28,000 in ransoms.
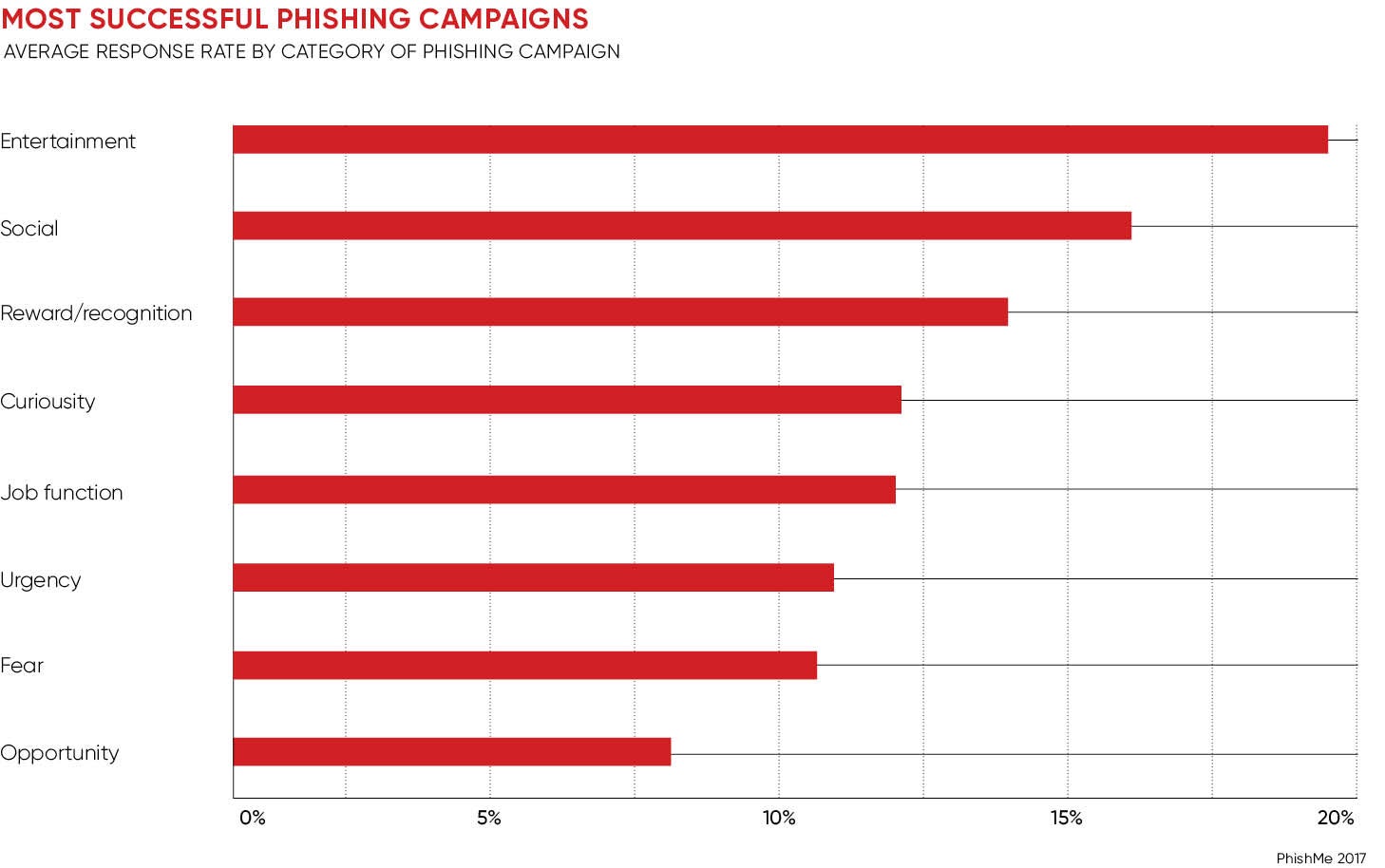
More commonly criminal social engineers will look to employ such intelligence gathering exercises to gain access to corporate networks and the valuable data stored within. The 2017 Verizon Data Breach Investigations Report shows one in every 14 phishing emails results in a malicious attachment or link being opened, and phishing is now present in one in five security incidents.
What’s more, the latest Enterprise Phishing Resiliency and Defence report, from social engineering educators PhishMe, reveals such attacks are up 65 per cent from last year. That’s worrying as phishing is the de facto tool of social engineering used by cybercriminals to hack humans and gain access to enterprise networks and the valuable data they contain. Some 15 per cent of these emails, according to the PhishMe report, will contain a malicious link and rely on entertainment, social media connections or reward as the emotional encouragement to click through.
So, how can the organisation best ensure that relevant employees are both aware of these threats and enabled to deal with them accordingly? To answer this, we first need to consider who those relevant employees are?
Graeme Park, senior consultant at Mason Advisory, says the simple answer is everyone. “It’s usually easy enough to elevate a user account to an administrative account or take control of another computer once they have access to the company infrastructure,” he says.
But some employees make more attractive targets, according to Mark Crosbie, head of trust and security at Dropbox, who warns that “those with strict business targets can be particularly at risk”. Sales staff might be susceptible to being lured with the promise of a business lead, especially as, Mr Crosbie points out, “they often work with external organisations, so giving the attackers added scope to mimic trusted sources”.
The C-suite should also look to itself as a potential target. The iPass Mobile Security Report suggests C-level executives, including the chief executive, are at the greatest risk of being hacked. This comes as no surprise to Alan Levine, cybersecurity adviser to Wombat Security, who points out that business leaders’ digital identities “can be golden keys to valuable personal and professional data”.
Employees can become the first line of cyberdefence, able to spot a socially engineered phishing attempt a mile off
Stephen Burke, chief executive at Cyber Risk Aware, recalls one chief financial officer (CFO) receiving a fake email supposedly from the chief executive and instructing him to wire money into an account with an explanation promised on his return from a meeting.
“The result was the CFO wired the money and the success of this fraud was down to the fact that the criminals knew the CEO was out of office,” says Mr Burke. How did they know? By simply calling the company, using publicly available information from social and corporate media, and establishing the chief executive’s agenda for the day on some believable pretence.
That’s not to say that people should be considered the weakest link in security; quite the opposite. Aaron Higbee, co-founder at PhishMe, argues that with effective conditioning techniques in place “employees can become the first line of cyberdefence, able to spot a socially engineered phishing attempt a mile off”.
So is awareness training the be all and end all of social engineering defence? “Advising people not to open suspicious emails, click on unexpected attachments or visit unvalidated websites only works if the attachment or email looks suspicious or the website is evidently a spoof,” says Amanda Finch, general manager of the Institute of Information Security Professionals. The problem is that the threat actors are getting better at what they do and pulling the right triggers to offset suspicion.
Steven Furnell, professor of IT security at Plymouth University, recommends using the LIST acronym to emphasise core cyber-principles is the best method of achieving this. Legitimacy: should you be asked for this information and would you normally provide it this way? Importance: what is the value of this information and how might it be misused? Source: are you confident that the source of the request is genuine and can you check? Timing: do you have to respond immediately? If in doubt, take time to ask for help.






