Unified communications (UC), collaboration and mobile technology are increasingly one and the same thing. Suppliers certainly agree for when even large enterprise technology behemoths, such as IBM, Oracle and SAP, start using the language of cloud, collaboration and small business units, and when desktop giant Microsoft bets Windows 10 on a mobile, collaborative future incorporating Skype for Business, then we can assume computing has left the corporate desktop for good.
This has changed the enterprise itself. For some organisations, “the office” is now a mindset and set of shared practices, rather than a place that people travel to. We used to talk of a work-life balance, but now it’s more a case of subtle and constant integration.
However, the fact that the once clear boundary between work and play is blurring means that security is becoming more complex in the always-on mobile world. Indeed, there is a sense that our legacy concept of “the enterprise”, with its 1990s roots in client-server computing, is breaking apart in the cloud.
Security must primarily be about policy, common sense, good practice and business goals; supportive technology comes second
The upside is increased collaboration, but when so much in communications is becoming a stream of personal choices rather than a clearly defined space, this poses a data security challenge, both for the organisation and for its customers, stakeholders and employees. For these reasons, security must primarily be about policy, common sense, good practice and business goals; supportive technology comes second.
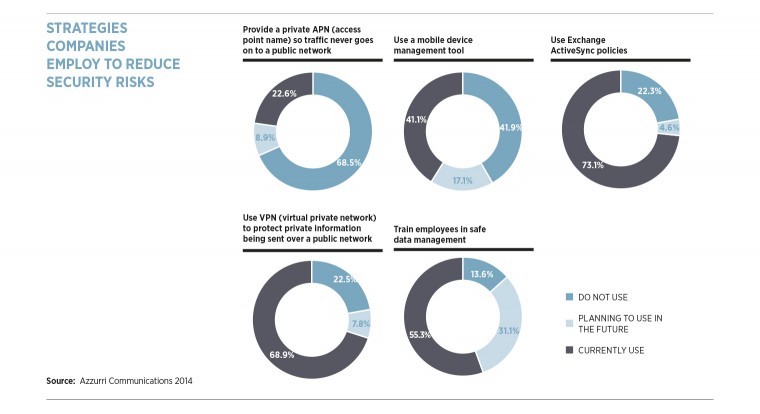
 Square one of the mobile UC security game is recognising that corporate data still belongs to the core organisation and not to the individual. It needs to be secured centrally and then accessed remotely by well-managed, rigorously enforced authentication.
Square one of the mobile UC security game is recognising that corporate data still belongs to the core organisation and not to the individual. It needs to be secured centrally and then accessed remotely by well-managed, rigorously enforced authentication.
Strong authentication and access control are a must and yet research consistently shows that “123456” and “password” or “Passw0rd” are still the most common passwords found online. Also, storing logins and passwords locally is only convenient when the device is in your possession; if it’s stolen or lost, any still-active sessions gift the finder an open door into the organisation.
Thanks to bring your own device (BYOD) schemes, people’s own choice of mobile phone or tablet is often the one they use for work too, so it’s important to emphasise that the organisation’s BYOD and data security policies don’t just apply in the office during traditional work hours.
Dispersed organisations of remote, mobile, flexible workers need to be held together by a shared mission, clear data-protection policies and common technologies, so not downloading apps independently of the IT team is core to the principle of UC – it’s called unified communications for a reason.
Security practices cover everyday behaviour because fallible human beings are always the biggest weakness when it comes to data security
Wrapped up in all this is the growth of so-called “shadow IT”, as employees and sometimes departments mix and match their own technologies informally. The temptation is clear as a world of new mobile apps and cloud platforms is out there, each promising to make the employee’s job easier. But any one of them might have been rushed to market and so be full of bugs or exploitable weaknesses. Some might even be malware.
However, business and IT professionals should see the desire to be creative as an advantage, signalling employees are enthusiastic and keen to do their jobs. So put together a suite of approved, standards-based tools that can be centrally managed and secured.
Mobile UC is also about common sense. Proactively managing and changing passwords is just one sensible measure, as is logging out of enterprise applications if your device is used by other people.
Other security practices cover everyday behaviour because fallible human beings are always the biggest weakness when it comes to data security. For example, don’t take part in private video-conferences or virtual meetings in public places, such as on trains, in cafés or in departure lounges. Anyone could be listening or taking notes, from journalists to customers, investors or competitors.
Similarly, don’t use free public wi-fi hotspots in cafés, hotels or even conference centres when engaged in collaborative business; use them at your own risk, not at your organisation’s. That tempting password-free hotspot might be a community resource, but equally it might be someone in the next room, scraping all the data from your device. Use the official channels.
For employers and digital-native employees, who have never known a world without mobiles and cloud platforms, security has a cultural dimension too. The millennial culture of openness, downloading, peer-to-peer sharing and constant communication may run counter to some organisations’ aims, not to mention their responsibilities to customers and their regulatory obligations.
Also, be aware that buying a collaboration tool doesn’t make you a collaborative organisation. To benefit from such tools demands a shift of culture, together with a supportive management team that isn’t threatened by flatter, less hierarchical workflows. As ever with IT, buy technologies to support business goals, not the other way around.
But, of course, security is a technology challenge too. “The enterprise” was once a secure silo with on-premise technology, a dedicated data centre, authorised hardware, enterprise software and a clear perimeter, the office firewall. But in many cases this has been replaced by something more nebulous – a fog of code and sometimes of responsibility too.
And just visible on the horizon is yet more disruption – the internet of things, the emerging world of interconnected devices made possible by IPv6 (internet protocol version 6). In this world a mobile device might be a tablet or a phone, but it might also be a car, a camera or telepresence robot, anything that can connect to a local network and then to the internet, or be controlled remotely by a smart device.
The implications for UC should be obvious. Over the next few years, international real-time meetings and collaboration on anything from simple documents to complex engineering projects will be the norm, and this means a huge variety of smart devices may be controlled remotely during these collaborations, from smart whiteboards to 3D printers.
Recent research by IBM has showed that countless smart devices can easily be hacked, including a car’s telematics unit, which was hacked via a modified MP3 file and disabled the car’s brakes, a building’s heating, air conditioning and security controls, and smart lighting, exposing a building’s wi-fi passwords.
In this new, interconnected world, IBM recommends use of a secure operating system with trusted firmware guarantees and a unique identifier, alongside secure authentication. IBM says: “While IPv6 is key to identifying ‘things’ on networks, ‘things’ also need a subscription to a trusted identity database. The concept of traditional authentication doesn’t apply.”
Data privacy protection is also essential. For example, with mobile payments starting to appear on smartphones, credit card information may be accessible to any devices that are linked to them, via wi-fi or Bluetooth, along with any corporate credentials that are stored on the device.
Data and transmission encryption are both essential, and yet it is astonishing how many of the cloud platforms that have been hacked or compromised in recent years contained unencrypted customer data, including log-ins and passwords.
In the mobile environment, strong application security is a must now that vulnerabilities arising from software bugs are commonplace, as the recent Heartbleed and Bash Shellshock cases have proved.
With mobile UC, always remember you carry the enterprise, along with everything and everyone connected to it, in your pocket.