Shadow IT is the use by employees of unauthorised cloud applications and services, such as Dropbox, Google Docs and OneDrive. This definition does not imply these apps and services are inherently dangerous or insecure, simply that they have not been authorised for use by the IT department and so are often invisible to security controls.
The Businesses @ Work report from secure identity management specialist Okta reveals that 56 per cent of apps used within the average enterprise are not provided and authorised by IT, and this is up from 48 per cent the previous year.
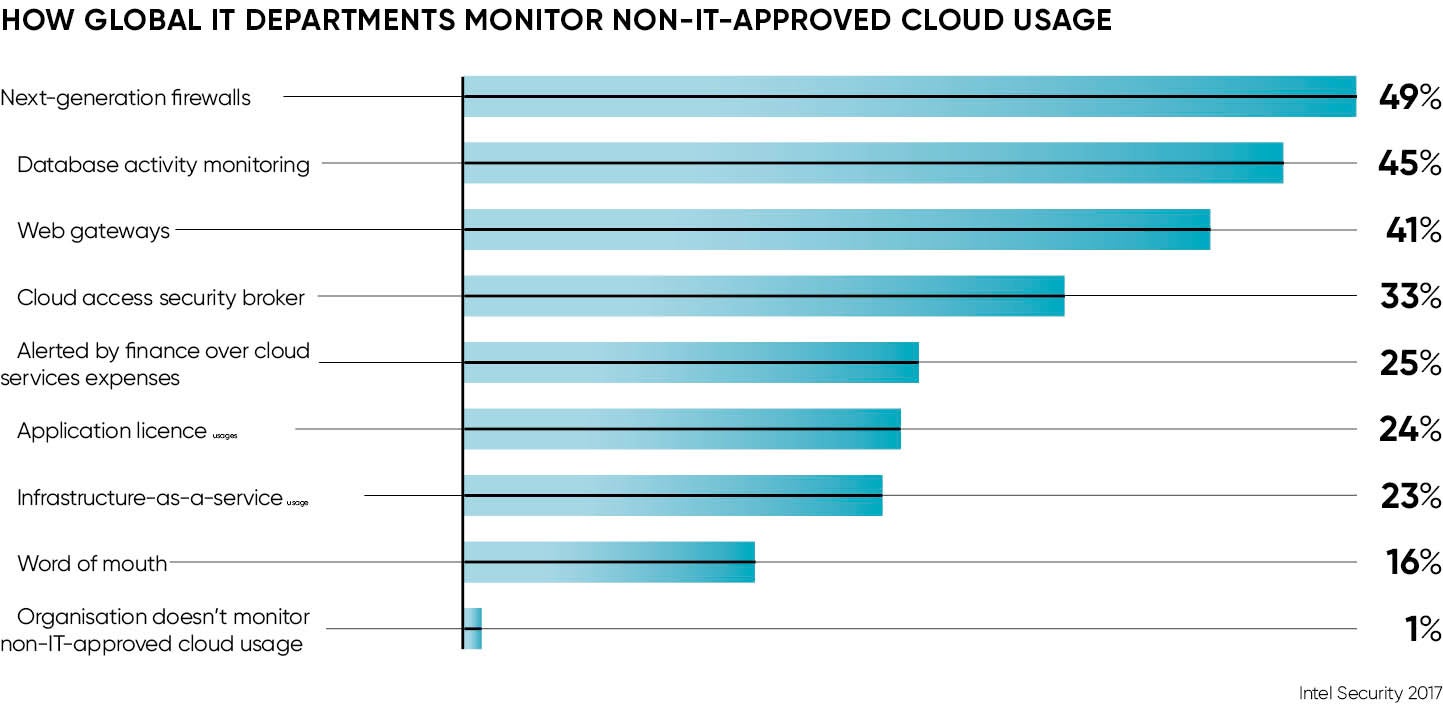
What’s more, the latest Cloud Security Report from Intel Security shows 74 per cent of UK businesses have a public cloud service in use that has been commissioned by departments other than the IT department.
That statistic of 74 per cent is interesting as it’s above the global average of 66 per cent. “In the UK at least, shadow IT is becoming almost the norm,” warns Raj Samani, chief technology officer for Intel Security in Europe, the Middle East and Africa.
Overall visibility of shadow cloud services dropped by 4 per cent last year, according to Mr Samani, so is this a problem needing to be tackled before we can ever really consider shadow IT to be a good thing? Indeed, should it be blocked altogether?
“A ban on shadow IT is not only pointless, it’s a ban on innovation,” says David Rosewell, head of strategy at Fujitsu, who adds that shadow IT is the democratisation of IT in practice.
“If companies haven’t any shadow IT purchases, then they should be worried. Either companies don’t have a handle on what’s going on or, worse still, their staff aren’t motivated enough to improve how they can harness IT to help the business,” he says.
As Nigel Hawthorn, chief European spokesperson at cloud security experts Skyhigh Networks, says: “When you block the well-known cloud services, you inadvertently push your users to the less well known and often more risky ones,” so achieving the direct opposite of the security goal.
If not a blanket ban, then what? Javvad Malik, security advocate at unified security management company AlienVault, advises the IT department works with employees to make them aware of their responsibilities in protecting data.
“Having a data classification policy complemented by a brand reputation monitoring and external threat intelligence service that can discover where either the corporate brand is being used without permission or intellectual property is publicly available,” is the answer, according to Mr Malik.
IT demands
Quentyn Taylor, director of information security at Canon Europe, sums it up best when he says: “There isn’t such a thing as shadow IT, there is only missed opportunity.” Mr Taylor agrees that IT is no longer the sole preserve of IT departments and argues that how to stop it shouldn’t be on the chief information officer’s agenda. He says: “Security teams are no longer departments of ‘no’, but are becoming departments of ‘how?’”
The concept of shadow IT really just highlights there’s a demand for services which do not yet exist within the organisation. “My advice would be to form a small group of people – at Canon we call it the Tiger Team – which proactively identifies user need and, if the solution meets it and works within legislative constraints, we go for it.”
Professor Steven Furnell, senior member of the Institute of Electrical and Electronics Engineers and professor of cyber security at Plymouth University, finishes where we started, with a definition of shadow IT. His is something that “helps to shine a light on services that the enterprise could benefit from”. Users are clearly doing it for a reason that isn’t likely to be purely based upon bloody-mindedness.
“They are doing something that they feel is aiding them to work,” Professor Furnell concludes, “so is it something that would benefit others if provided in an official and supported guise?” Organisations should grasp the opportunity that shadow IT provides, rather than stand in the way or turn a blind eye.






