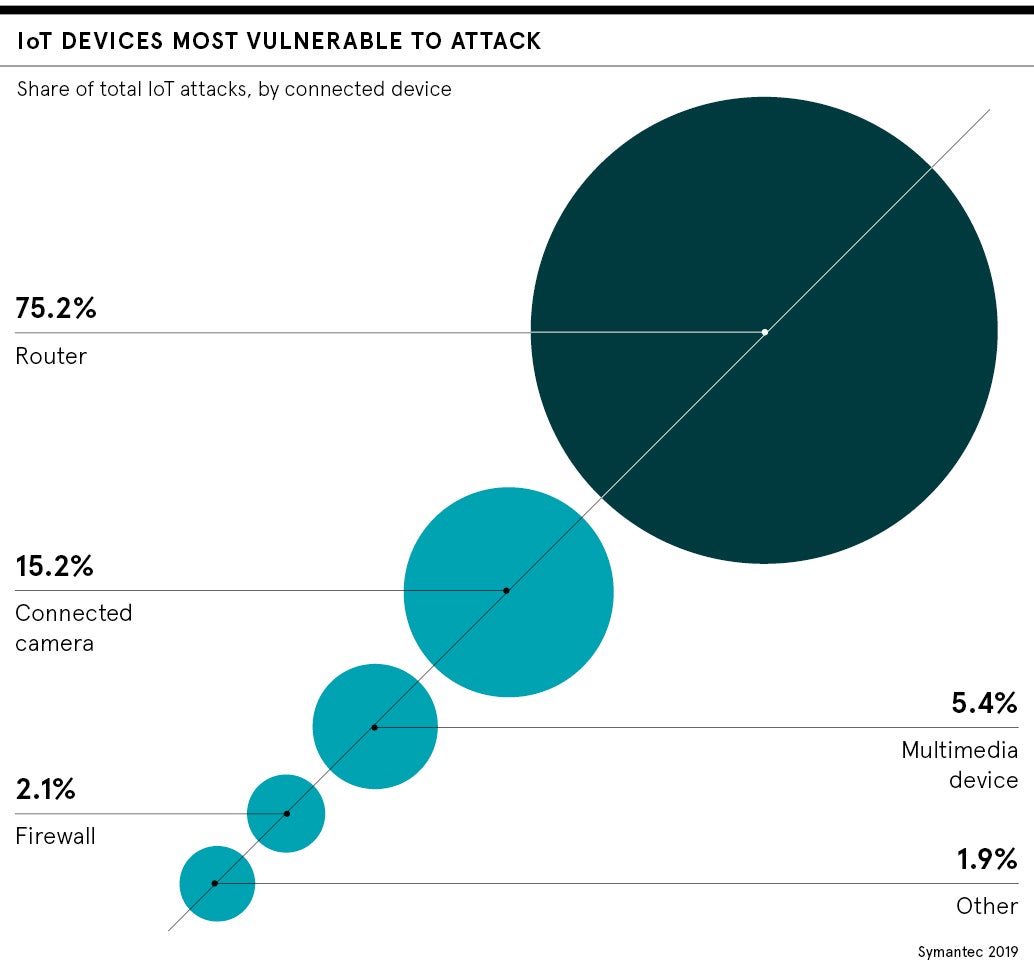
There’s something deeply unsettling about peering into other people’s insecure webcams.
It was a January evening and I was hanging on Twitter with Luke Stephens, an ethical hacker, who was sending me links he’d found to webcams open online. The devices didn’t have password protection turned on by default and their owners apparently didn’t realise this. Like so many internet of things (IoT) devices, the cameras were an insecure mess.
I saw something that allowed you to change the flow of water through a city. It was wide open
I saw one camera that looked out in the lobby of a building in India and another in a Spanish plaza. Then, most alarmingly, I found one in a house in Germany showing a clear view of what appeared to be a bedroom, with a cabinet half open and a small table with a few bottles of water on it. Nobody was in view. I immediately closed the browser window, feeling like a creepy voyeur.
How had Stephens and I found all these open, insecure webcams? Not through any nefarious hacking. We were using Shodan, the “search engine for the internet of things”.
Shodan is a tool that lets anyone search for IoT devices online. If you hunt for a particular piece of hardware – a new voice-controlled thermostat, say – it will provide you with a list of them anywhere in the world. Or if you type in the IP address of your firm or house, Shodan will show you whether you have any public devices online.
Much as Google “crawls” the internet, pinging every webpage to create a massive list of them, Shodan crawls the universe of internet-connected devices. It doesn’t actually log on to them; it just records any metadata they publicly broadcast.
A search tool for vulnerable devices
You might imagine that Shodan would be a choice tool for black-hat hackers. A search engine, ripe with possibly vulnerable targets.
But in reality, it’s mostly used by white-hat security professionals, to help them keep their companies safe. Shodan and other sites that have blossomed in the wake of its success have become a crucial way to figure out whether any of their online devices are accidentally insecure.
“Hackers will find vulnerabilities,” as Shodan creator John Matherly says. “What’s important is that you respond in a timely manner and fix the bugs.” He launched the tool ten years ago and now 80 per cent of his customers are security professionals within Fortune 100 firms.
What types of things do white-hat hackers find on Shodan? A dizzying array of leaky devices. US-based security researcher Nate Warfield has found devices that were vulnerable to ransomware attacks and even Monero mining attacks when botnets hijack a business’s devices and use them illicitly to mine cryptocurrencies.
Plus, new vulnerabilities are discovered daily, so whenever Warfield hears of some new leaky, piece of software or hardware, he can quickly use Shodan to check if his clients are exposed. “It’s extremely useful when you need to quickly assess the risk,” he notes.
Having even one IoT device that’s vulnerable can become a critical weak point for a firm. Recently, Tom Lawrence, founder of security firm Lawrence Systems, ran a test to show how this works. Using Shodan, Lawrence found an exposed port on a device at the firm and discovered an employee’s name on it. Using the name, Lawrence says: “We found some records on them. We found their LinkedIn.” This led to the employee’s mobile number, which allowed Lawrence to generate “a phishing attempt through a password reset that you send to a fake link on there”. Thus he demonstrated how you could break into a firm through one leaky device.
Finding weak points in the IoT ecosystem
Many firms use Shodan to set up a monitor, a sort of Google alert, which pings if Shodan finds a vulnerable IoT device suddenly alive on their network. Nathan McNulty, who works in security for a school district in Oregon, recently had one such alert ping when an employee put a server online and, through a single typo, left it exposed. “Fortunately, it had no data on it yet when we found out,” says McNulty, “but it could have been very bad.”
Other white-hat hackers use Shodan to hunt for so-called bug bounties, checking major companies for vulnerabilities, then alerting the firm in the hope of a reward. Stephens was recently prospecting for bug bounties when he found a company with a device so insecurely configured that it “allowed any hacker to gain full control of that system”, he says. “This level of access also would have made it easy to read from a database, which contained personal details of all customers.”
Sometimes security professionals, just for curiosity’s sake, will go on a Shodan safari, poking around to see what unprotected devices are around. They quickly stumble across alarming stuff. Personal webcams may be the least of the world’s problems, but governments worldwide are leaving mission-critical systems lying around utterly exposed, according to Matherly.
Security expert Daniel Miessler says: “I saw something that allowed you to change the flow of water through a city. It was basically opening and closing the ports that control the dam structure. It was wide open.” He’s also found exposed “power control systems, water control systems, manufacturing plant controls: the nastiest stuff you can imagine”.
Industrial control systems, open for hacking
Warfield adds: “I could write a novel on the interesting and terrifying things I’ve found.” These include an insecure air-conditioning system for an Asian skyscraper and a remote-controlled fire-suppression water cannon at a port in the South Pacific.
As Matherly concludes: “We live in a crazy world.” Most white-hat hackers seem resigned to the fact that firms, and individuals, aren’t going to stop putting IoT hardware online. So they offer this important advice: if you buy an IoT gadget, immediately change the password, update the software and put it on a separate network. That way, if it gets hacked, it won’t be a stepping stone to your email, financial databases or other personal details.
A search tool for vulnerable devices
Finding weak points in the IoT ecosystem

