Consumer demand for internet-connected devices and the software applications that power them has rocketed in the last ten years. Smart applications now spread beyond smartphones into other devices, with web-enabled television, doorbells and security cameras increasingly commonplace. Software is a pervasive and crucial driver of innovation in commerce, helping organisations to be more agile and competitive.
The functionality of these devices and applications are determined by source code written by developers. According to the AppSec Market Report, around 111 billion lines of new software code were created in 2017. Within that massive volume of new code inevitably comes millions of software vulnerabilities and the security problems compound themselves with age.
The growing reliance on software in both business and society means data breaches are more impactful than ever and hackers are actively targeting vulnerabilities in the code. In Verizon’s Data Breach Investigations Report 2018, web applications were identified as the most common source of data breaches and security incidents.
“Software applications are the prime target for attackers who want to get hold of an enterprise’s assets and data,” says Paul Farrington, chief technology officer, Europe, Middle East and Africa, at Veracode. “Web and mobile applications account for more than a third of data breaches, and attacks at the application layer are growing by about 25 per cent annually.”
While 20 years ago software was mostly developed in-house using custom code, Gartner forecasts that seven out of ten applications are now running on open source databases.
Developers face overwhelming pressure to push out more software in shorter timeframes. Open source libraries can help by providing pre-built pieces of code that deliver specific functionality without having to build it from scratch. Consequently, 90 per cent of the code in many applications may originate from open source libraries. Open source software enables developers to fulfil business requirements more quickly and at less cost, but also introduces new risks.
When software is released as open source, it means the original author intends to give the code to developers to use freely, study and enhance. The amount of collaboration these projects can foster brings forward some of the greatest advancements in tech and it makes the software more accessible for individuals who cannot afford licensing fees.
It’s really key to ensure developers not only think about the theoretical risk, but are also given tools to highlight the proven risks that exist in the software
The benefits of open source code can be so alluring that businesses forget about the risks involved with using public, unvetted chunks of software throughout their applications. Vulnerabilities in open source code are prized by hackers simply because of the prevalence of their use. Once a hacker discovers a vulnerability in a widely used open source package or library, they can exploit potentially thousands of systems running that code, amplifying by many degrees the impact of the vulnerability.
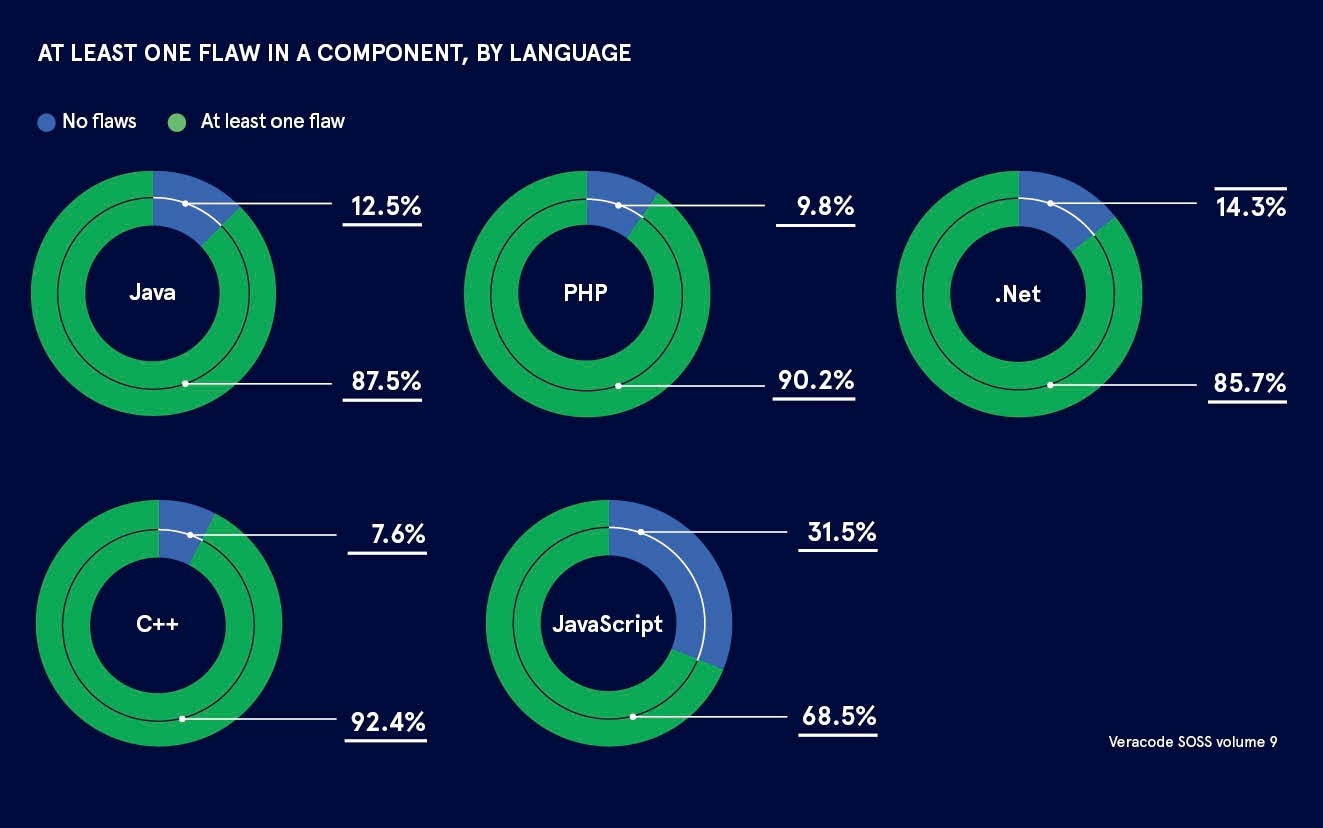
According to Veracode’s State of Software Security report, 88 per cent of Java applications contain at least one vulnerable open source component. This is noteworthy because just a single vulnerability in a piece of open source code can hit hundreds of thousands of applications.
“The open source community is really exploding and the desire for businesses to move faster is encouraging developers to make use of open software, which reduces the cost for enterprises and means delivery timelines can be hit faster than ever before,” says Mr Farrington, who predicts there are more than five million unique open source components that exist in various software repositories developers interact with. “Soon, this will become hundreds of millions because of the rate of contribution from developers,” he says.
Developers are no doubt aware of the security flaws in open source software. For example, the Apache Struts vulnerability was behind the massive data breach that exposed the personal information of 143 million Americans in March 2017. But while they may appreciate the imperative of creating secure code, knowledge of how to do so is lacking.
Education and awareness will ultimately empower development teams to improve how they create secure code. Veracode provides tools that enable developers to identify and correct security defects within seconds of writing code, while also telling them whether or not the open source building blocks they are using have any vulnerabilities in them.
Automation technologies such as artificial intelligence and machine-learning are accelerating the ability to look for defects in software, but it will be an appropriate balance between machines and humans that is most successful. While computers are excellent at looking for the traits of potential defects in data at speed and scale, they can’t do without our human ability to prioritise how to address and remediate flaws.
“We use machine-learning to identify and pinpoint potential vulnerabilities with ever-increasing accuracy,” says Mr Farrington. “However, humans are great at finding the sequence of steps hackers must undertake to compromise that system. We use the appropriate blend of automation and human ingenuity. We call these people manual penetration testers, looking for security defects to prove they exist in systems.”
Developers must ultimately think about where the software will sit once it goes into production or lands on a user’s device. Applications may exist in hostile environments, far longer than originally envisaged, and hackers may do anything to subvert them. As such, developers should seek an understanding of secure code and work in tandem with security teams to remove friction from the development process.
“As the use of containers continues to drastically reduce the time required to deploy and scale software, we are at the forefront of developing techniques to ensure we secure the applications that exist in containerised environments,” says Mr Farrington. “However, addressing the problem at source, when the developers actually write the code, is going to be how we address the problem at scale.
“It’s really key to ensure developers not only think about the theoretical risk, but are also given tools to highlight the proven risks that exist in the software. Veracode pinpoints what we call the ‘vulnerable methods’ so we can show developers the line of fire between the code they write and the security exploit that is just waiting to happen in the open source software. That’s a game-changer for software development teams who don’t have time to deal with noise.”
To get a clear picture of the state of software security, including data on open source risk, which vulnerabilities peers in your industry are finding most often, and how organisations are reducing their software risk, please download Veracode’s State of Software Security Volume 9 at www.Veracode.com/sossreport



