Many IT and business leaders will be keen to know where the next big threat will come from in 2018, but unfortunately cybersecurity is not an exact science. What we can say, though, is that we’ve certainly not seen the last of digital extortion, business email compromise (BEC) and cyber-propaganda campaigns.
With cybercrime happening on an industrial scale, we must find innovative ways to combat an increasingly agile and resourceful enemy.
YEAR OF RANSOMWARE
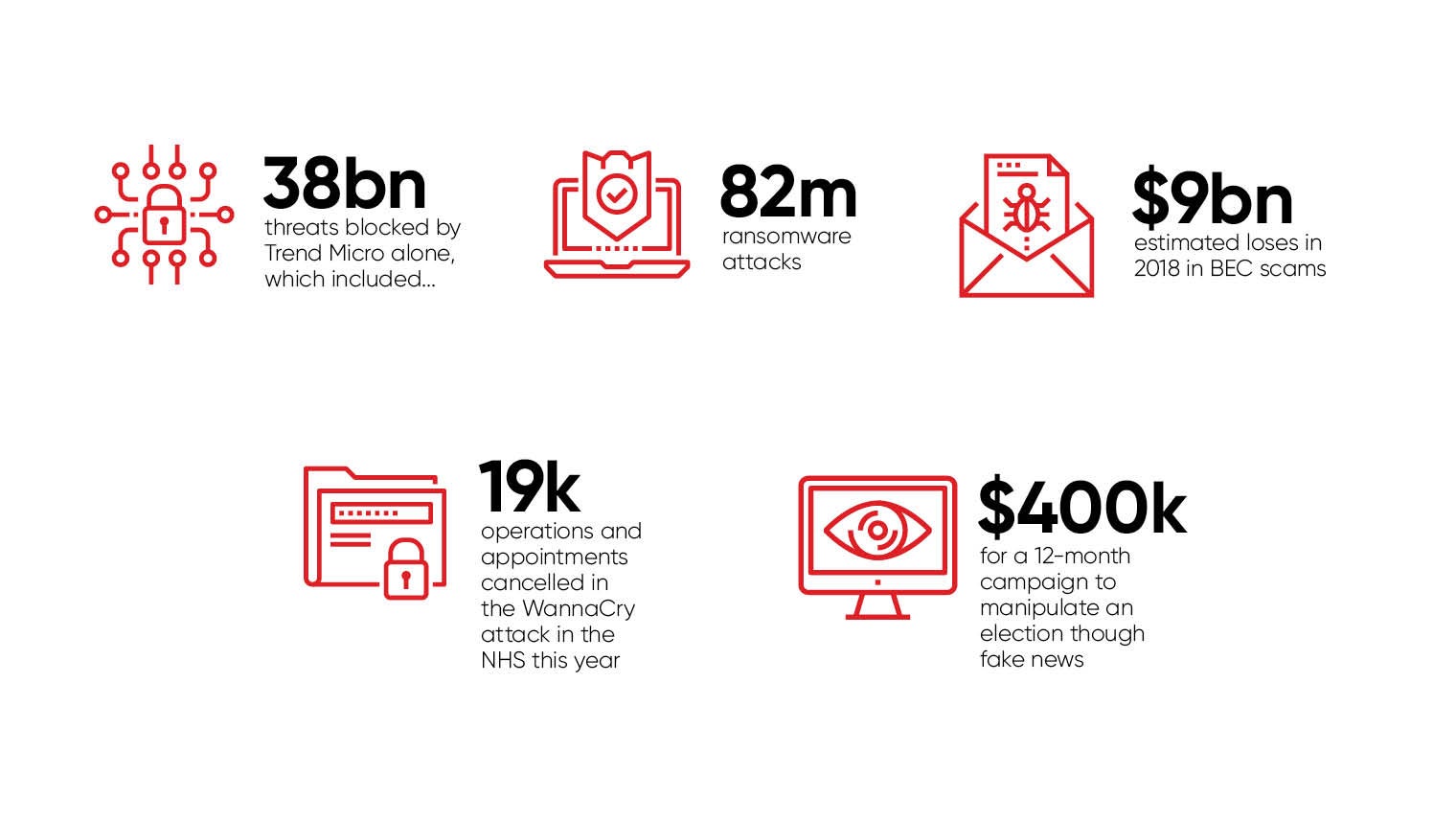
Just how big is the scale of the cybersecurity challenge facing us? In the first half of 2017 alone, Trend Micro blocked more than 38 billion threats, including 82 million ransomware attacks. As predicted, ransomware was adapted in 2017 for maximum impact. We saw the result of these efforts in the catastrophic WannaCry and NotPetya campaigns, which caused firms such as global shipper Maersk, FedEx subsidiary TNT and Nurofen-maker Reckitt Benckiser hundreds of millions in losses.
WannaCry, in particular, caused chaos in the NHS, with an estimated 19,000 operations and appointments cancelled. Those behind NotPetya, meanwhile, showed an even more sophisticated approach, using ransomware to disguise what was in reality an attempt to destroy the systems of its initial Ukrainian targets.
The bad news is that the ransomware-as-a-service or RaaS model will continue to drive the growth of this cybercrime sector in 2018, enabling even non-technical hackers to generate profits by exploiting poorly secured organisations.
DIGITAL EXTORTION DEEPENS
However, online extortion will get even more insidious over the coming year as the bad guys go straight for the money. The old model of launching information-stealing malware to compromise customer personally identifiable information is still favoured, but it can leave cybercriminals hanging for months or even as long as a year before they can finally monetise their efforts. Even then, many may find that their return on investment (RoI) from such campaigns is disappointing. Contacting the victim organisation directly to extort funds is far quicker and arguably more likely to result in success.
We’ll see the hackers increasingly targeting those more likely to pay up, such as industrial operations run by utilities providers
Thus we’ll see the hackers increasingly targeting those more likely to pay up, such as industrial operations run by utilities providers, where any ransomware-related outages could have a major impact on the populace. We may even see cybercriminals using the threat of General Data Protection Regulation fines to extort companies, potentially by stealing their customer data and then offering to delete it if a ransom is paid, as Uber did. Organisations should be aware that the headline fine of 4 per cent of global annual turnover or £17 million is not automatic and will only be levied in extreme circumstances if little effort has been made to secure systems.
However, by the same token, if attackers find a particularly poorly secured organisation, their extortion may well work. Some cursory intelligence gathering to establish the annual revenue of the company, and therefore how much in GDPR fines it may be facing, could further help them to tweak their ransom price.
BUGS ARE EVERYWHERE
Something else we learnt from the past year is that software vulnerabilities are increasingly the weakest link in the corporate security chain. Even flaws which had been patched by the manufacturer ended up being exploited to devastating effect months later. Just consider the Windows SMB vulnerability, which Microsoft issued a fix for in March, but enabled WannaCry to spread to hundreds of thousands of users around the globe within hours. Cybercriminals will see the impact these exploits had and will try their luck with many more known vulnerabilities in 2018, hoping that organisations will have failed to implement best-practice security.
A comprehensive patch management programme is essential to ensure all systems are protected as soon as an update is made available. Things get trickier in critical infrastructure where IT managers may not be able to patch because of legacy systems or else don’t want to risk the downtime associated with testing. That’s where virtual patching can come in handy, protecting systems until they’re ready to be patched properly. Machine-learning can also help organisations spot threats early on, with more accuracy than traditional solutions.
EMAIL SCAMS HIT HOME
It’s also fair to say that 2017 was the year of BEC scams and 2018 is likely to see total global losses hit a staggering $9 billion. It’s proof again of cybercriminals going straight for the jugular with direct tactics designed to net them the biggest RoI possible. Many BEC attacks are made even harder for traditional security filters to spot because they typically don’t involve the use of malware. Instead, a chief executive’s email address is forged and a member of the finance team targeted with classic social engineering in a bid to trick them into transferring large sums of money outside the company.
Part of the answer lies in raising awareness among staff of such scams. Employees are your other major weak link in corporate security, so all staff including temps should be trained in a continuous year-round programme. Try to move away from theory and technical jargon, and towards exercises using real-world situations and everyday language.
POWER OF MACHINE-LEARNING
Machine-learning once again can be useful in helping to prevent BEC. Think of it as a kind of forerunner to full artificial intelligence. Its value lies in being able to analyse huge amounts of data to find the needle in the haystack that might indicate a major threat. But to be successful, any machine-learning-based security tool must be properly trained. You need good quality data, and lots of it, to help the system establish a baseline of “normal” behaviour so it can flag with a high degree of accuracy when something doesn’t look right. That could be anything from a BEC email scam or a vulnerability exploit in a ransomware-laden email.
High-fidelity machine-learning should be a key component of your layered security response in 2018.
But be warned, while the white hats are increasingly promoting machine-learning as a way to combat advanced threats, the cybercrime community may also be tapping publicly available tools to find security gaps and zero-day exploits.
GET REAL ABOUT FAKE NEWS
As we’ve discussed, the success of staff security awareness programmes will have a major bearing on the threat landscape in 2018. But we also need to think about educating society as a whole, not just on cybersecurity, but on spotting fake news and cyber-propaganda. Earlier this year we uncovered for the first time the sheer size of this underground market, where a 12-month campaign to manipulate an election can cost as little as $400,000 (£315,000).
In many ways, the impact of fake news is the one cyber-related threat that really does have the potential to cause the most damage to our society and way of life. So as we go into 2018, with key mid-term elections coming up in the United States, it’s never been more important to think before you click.
For more information please visit www.trendmicro.com
YEAR OF RANSOMWARE

