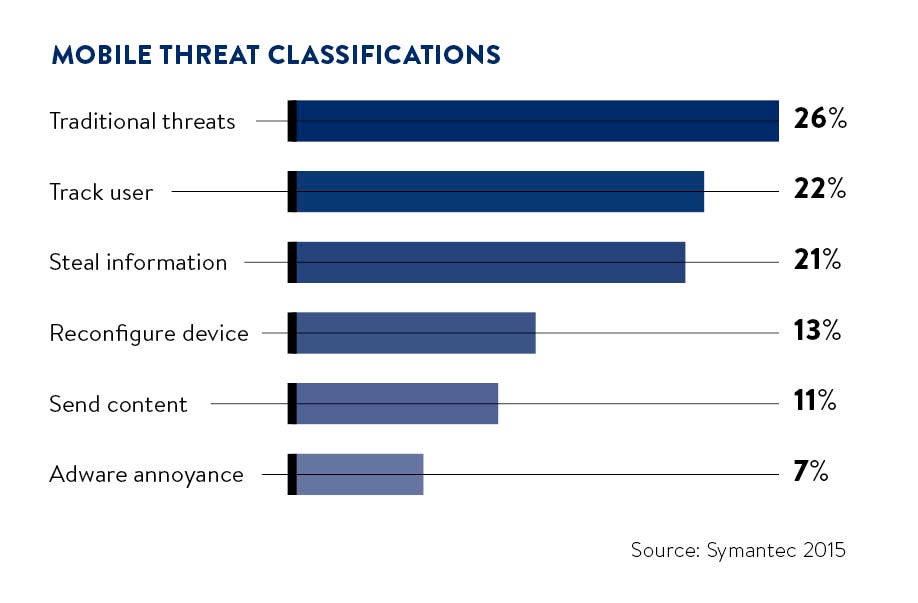
By 2020 a staggering 4.6 billion people will own a mobile device. This figure, from industry trade body the GSMA, shows just how ubiquitous mobile phones have become in a few decades.
These devices are changing the way we work and how businesses operate. Mobile phones and tablets are replacing landlines and PCs, with everyone, from executives to field engineers, carrying what amount to miniature computers.
But our addiction to mobile devices brings with it security risks. As businesses depend more on mobiles, so the devices will carry evermore sensitive applications and data.
A phone can be the keys to the kingdom – it is a really rich target
And, because mobile phones and tablets are very personal devices, often bought and owned by the worker, companies may have few controls over how or where they are used. But companies cannot tell their employees to go back to their old ways of working.
Looking down mobile devices
“You can’t roll this back – you have to support mobile,” says Kevin Bocek, chief strategist at security firm Venafi. “Everything is touching mobile now. If you have a mobile app that talks to something in the datacentre – that is mobile.”
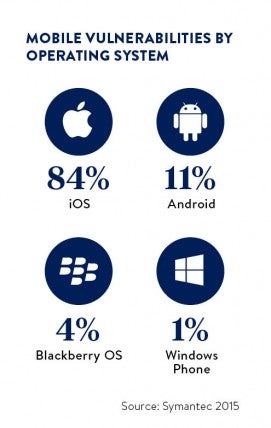 This raises the risk that if hackers or other criminals obtain a mobile device, or can break into it, they can use it to penetrate deeper into a company’s network.
This raises the risk that if hackers or other criminals obtain a mobile device, or can break into it, they can use it to penetrate deeper into a company’s network.
And, although mobile devices are actually more secure than early PCs, there is growing pressure for the industry to give security forces and law enforcement agencies “back doors” to the devices which bypass security, as the ongoing dispute in the United States between Apple and the FBI shows.
“A phone can be the keys to the kingdom – it is a really rich target,” cautions Ben Johnson, chief security strategist and co-founder of Carbon Black, also a security firm. “The people using tablets and phones are often the executives, the people who have the most sensitive material.”
This, he suggests, means organisations need to act now to lock down mobile devices, before they present a real risk to security.
[embed_related]
Protecting your business
Some of the steps businesses can take to secure their mobile devices are similar to measures for securing PCs – installing anti-virus software, ensuring operating systems and applications are up to date, and making sure employees set strong passwords and PINs.
The mobile industry itself is also acting to make their devices more secure. BlackBerry, for example, recently launched the PRIV, a highly secure phone based on the Android operating system.
Apple already encrypts data on its handsets as well as messaging services such as Facetime, one reason for its current dispute with the FBI.
There is a wide range of applications for mobile device management which allow IT directors to lock or wipe lost or stolen phones. These range from free tools, such as Apple’s iTunes, to more comprehensive systems from Microsoft and specialist companies such as MobileIron.
Companies, though, might be reluctant to eat into their IT budgets to bolster mobile security, especially as the number of security incidents attributed to mobile devices remains small.
Accessing personal data
Verizon, the US-based mobile operator, calculates that 0.03 per cent of mobile devices were infected with any truly malicious malware. But the threats to mobile devices are not limited to the type of high-profile virus attacks that affected desktop computers ten years ago.
Instead, hackers are looking to steal business data, gain access to companies’ networks, to accounts belonging to “privileged users”, such as IT administrators, and possibly capture personal data, such as a user’s location and passwords, or financial information, for identity theft and other criminal purposes. According to Verizon, more than five billion Android mobile applications are vulnerable to attack.
And businesses might be wary of installing mobile management applications for legal or contractual reasons. If an employee brings a personal device to work, companies will have fewer options to control that device than if they buy the workforce company phones.
In some countries, especially Germany, there are strict rules on employee monitoring and this can also make it hard to ensure mobile security.
As a result, some businesses are reacting by buying more devices for staff and moving away from bring-your-own-device programmes that allow personal mobile kit at work.
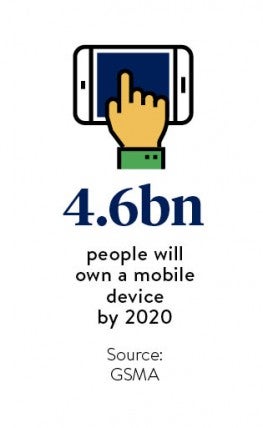 But even then, there are risks associated with using mobile devices that are simply different to the risks posed by a PC on a fixed network and those risks might be growing. “A desktop PC is hardwired to the network. Mobiles access thousands of different networks and they are out in the field doing that,” says Chris Underhill, head of IT and security at consulting firm CSP.
But even then, there are risks associated with using mobile devices that are simply different to the risks posed by a PC on a fixed network and those risks might be growing. “A desktop PC is hardwired to the network. Mobiles access thousands of different networks and they are out in the field doing that,” says Chris Underhill, head of IT and security at consulting firm CSP.
And, not only do phones have computing power on par with a PC of just a few years ago, but they have far more sensors, from the camera and microphone to an accelerometer that records how fast the device is travelling.
“There are new ‘threat vectors’ that need addressing, which tend to accompany mobile – radios, social and sensors,” says Rob Bamforth, of industry analysts Quocirca. “Does that make mobile security more difficult? Probably not, but the risks are less tangible so perhaps easier to miss or ignore. That’s what makes them more of an issue.”
Jon Collins, industry analyst at GigaOm, says: “Mobile devices have blown any traditional ideas we might have about security right out of the water. Ultimately the focus needs to be on data.
“First that is in terms of both what personal information an individual is prepared to give up via the device and via apps. Second in the corporate sphere, it is what corporate data should be accessible, and therefore potentially vulnerable, on the device.”
This suggests that companies might need to restrict the applications staff run on mobile devices, especially personal ones, and also limit mobiles’ access to sensitive networks. But few experts suggest that companies can roll back mobile working.
“I can’t see any executives pushing back on mobile,” says Kris McConkey, who heads the cyber threat detection and response team at consulting firm PwC. “There is a lot more recognition that the next generation [of employees] expects to be able to work more freely. But that also means a growing ‘attack surface’.
“Firms should take the same basic approach they do to a lot of security issues. Limit privileges, and keep apps and operating systems up to date. They should think about what introducing mobiles or putting business applications on them does to the security landscape.”
Looking down mobile devices

Protecting your business