When it comes to security, there is a cloud of mistrust hanging over the boardroom. Survey after survey reveals that security, or rather the perceived lack of it, is the single biggest factor preventing business from migrating to the cloud. But how accurate is this perception?
Jamal Elmellas, technical director at secure cloud provider tolomy, points to recent research from the Cloud Industry Forum (CIF) which highlights the discrepancy between perceived threat and actual risk.
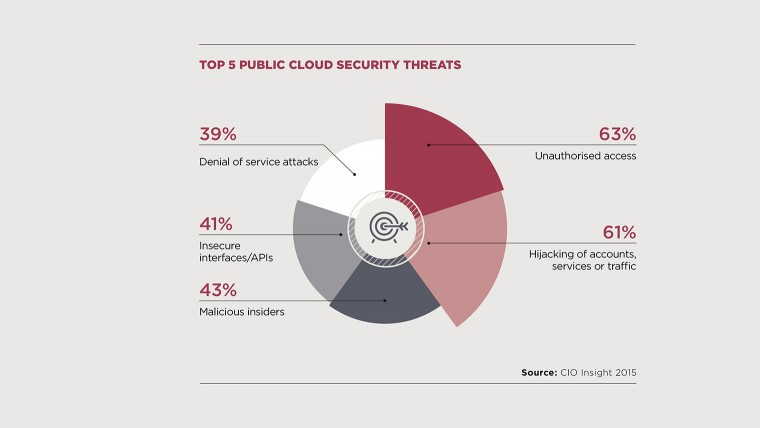
“CIF surveyed 250 senior IT and business decision-makers in the UK with 61 per cent reporting concerns over data security,” Mr Elmellas says. “Only 2 per cent had experienced a cloud-related security breach.”
The consequence of this conflation is two-fold in that businesses not only miss out on the budgetary benefits of the cloud, but also quite often remain less secure than had they actually migrated there.
Security provider SecureData’s cloud services director Alan Carter argues that too many businesses are “guilty of an overinflated view of their own capabilities” where the on-premise physical server room is seen as inherently secure in a way that virtualised servers cannot be. This represents a “cloud equals danger” mindset that is as outdated as it is misguided.

“Cloud services are, by definition, more abstracted and intangible,” says Scott Nicholson, information assurance and security manager at cloud integrator Adapt. “Yet in reality, a provider that specialises in delivering cloud services is likely by definition to have stronger security and operational controls, and more experience than an IT department functioning as a single business unit.”
Not that this means the cloud is concern free, but most concerns are actually the same as apply to on-premise networks – breach, denial of service and malicious insider risk.
Perhaps the most relevant when it comes to the cloud is the small matter of personal data; specifically the consents obtained and where the data is stored. Especially so in the light of the upcoming European Union Network and Information Security cyber-security directive and the General Data Protection Regulation, both of which are set to be fully implemented by 2017. These specify that organisations have to handle EU citizen personally identifiable information securely or face a fine of up to 5 per cent of global turnover in case of breach.
Businesses using cloud services have to know where consumer data is being stored and how it’s protected
“Businesses using cloud services have to know where consumer data is being stored and how it’s protected,” warns Keith Bird, UK managing director for security vendor Check Point. Most of these concerns can be dealt with by the use of a hybrid model where personal data is stored within a private cloud within the European Economic Area.
“As most cloud providers are based in the United States there are particular issues with processing of personal data by those providers,” says Richard Nicholas, an IT lawyer at Browne Jacobson. “In addition to ensuring US providers have safe harbour certification, the certificate should be checked to ensure it is up to date and that the cloud provider commits in its contract to comply with the safe-harbour principles for the term of the contract.”
Regulation and compliance remain a bigger cloud hurdle than security FUD – fear, uncertainty and doubt – and this is most evident in certain industry sectors. ICT solution provider NTT Communications undertook research which revealed that 87 per cent of financial service companies and 63 per cent of retail distribution and transport companies didn’t plan to migrate their most important applications to the cloud due to security, governance and compliance concerns.
Clive Gringras, head of technology and a partner with international law firm Olswang, advises that players in these heavily regulated sectors need to “engage with their regulator to ensure it appreciates the benefits of cloud computing and is not allowing old rules to unnecessarily hinder a move to the cloud”. Furthermore, Mr Gringras insists that a stock cloud provider answer of “it’s for you to determine whether we fit within your regulatory regime” is simply not acceptable.
So how should a cloud service provider be answering the compliance question? This rather depends if you are asking it of the right provider in the first place, as there are those that will specialise in particular industry sectors and therefore be familiar with regulatory nuances.
“Customers should ask the cloud service provider if it has any big-name clients running mission-critical applications in the cloud and for demonstrable evidence on how regulatory needs are met,” says tolomy’s Mr Elmellas, who doubts there will be any real traction in the finance sector until cloud solutions emerge that are built around specific financial regulatory requirements and markets. “Financial services in general have some of the most talented security resources on the planet,” he says, “so it’s not the resource that’s the problem, it’s the way in which risk is reported and managed.”
Retail is dominated by Payment Card Industry Data Security Standard compliance, and any gaps between the standard and the capabilities of technology inevitably increase risk. “The latest versions of the standard have started to address cloud-specific concepts so the gap is closing,” says managed hosting and cloud provider Memset’s security manager Thomas Owen, who also warns that the extreme cost-focused nature of retail also means regulatory concerns often get steamrollered anyway.
Ian Tomlinson, chief executive of cloud-based retail technology vendor Cybertill, is well placed to comment on the security fears of the sector. “There is some reluctance through disruption to service, but resistance to this is waning,” he says. “A critical point that does affect retail is the geographical location of the servers hosting the software applications in the cloud.”
This need not be a barrier to adoption though, as Luke Forsyth, vice president in the information management services practice at business advisory firm AlixPartners, points out. “While many of the security challenges of cloud computing can lay in the geographic distribution of information resources,” he says, “retail organisations have some natural advantages because these are familiar challenges as the nature of their business has often required a large number of locations.”
Ultimately, when it comes to security, the cloud changes nothing and the broad brush strokes of a secure environment remain the same no matter where the canvas is hung. But how can you best mitigate risk when migrating from on-premise to the cloud? Whenever the phrase “top tips” pops up above the parapet, having a handy acronym to call on is always useful. In the case of securely migrating to the cloud that acronym is ATMOSPHERE:
Accreditations: ascertain any accreditations that your proposed service provider holds, specifically ISO 27001 (the internationally recognised standard for information security) and ISO 27018 (the new cloud data privacy standard).
Tools: do your research and you will find there are plenty of tools to help you remain secure during a cloud migration, everything from risk auditing through to encryption key management.
Monitoring: Regularly monitor and audit any externally provided services, and ensure strong access controls to your data with sufficient logging to reveal when your data has been accessed and by whom.
Onus: contractually agree areas of responsibility between your organisation and service provider to reduce any potential disputes; ensure service levels are defined, agreed and monitored throughout the migration.
Specialise: if your industry is highly regulated or has particular security needs, perform due diligence and find a cloud provider that specialises in your sector.
Policy: following a policy-based separation of duties is key to migrating data safely to the cloud, preventing ‘privileged status abuse’ and advanced persistent-threat-style attacks.
High availability: ensure you have high availability baked into the cloud infrastructure with a secure back-up and recovery solution, should the worst happen during the migration process.
Environment: be aware of where your data is being hosted and stored – is it offshored or is multi-tenanted hosting provided, if so with which other organisations and what are their related threats?
Risk assessment: audit the sensitivity of your data, any regulatory considerations and the requirements for access to that data; once you properly understand the risk and operational needs, identifying appropriate cloud security controls becomes much easier.
Encryption: the best way for companies to remain secure and compliant with most data residency laws is to encrypt data held in the cloud environment with encryption keys that are unique to specific jurisdictions, and are controlled from those jurisdictions.
CASE STUDY: CHASE SOLUTIONS ARE SECURE ‘THIN’ CLIENTS

Chase Solutions is a field services organisation working with utility companies, banks and debt collection agencies across the UK. With 30 full-time staff based at its headquarters in Blackburn, Lancashire and a network of some 600 field agents, it needed to find a flexible hosted desktop solution to enable its management to work smarter while on the road.
Mindful of the need to meet the strict security and legal compliance requirements of both clients and industry regulators, the search led to cloud services provider iomart.
Chase Solutions knew that a hosted desktop would be the perfect technology, allowing management to work on the road without having any important data actually held on the devices they were using.
“The whole solution is hosted in iomart’s cloud in their fully compliant and accredited data centres,” says Michael Wolfenden, Chase Solution’s director of operations. Far from being worried about negative security implications of such a move, the cloud has actually strengthened the security posture of the company.
The laptops used by the regional managers have a minimal operating system based on Linux that is securely configured to only allow access to the cloud environment via thin client software VMware Horizon. Being “thin client” means that only screen images, keyboard and mouse instructions are transmitted between the laptops and the cloud. No data leaves the iomart data centre and therefore there is no risk usually associated with laptops and data stored on their internal drives.
Steve Riley, the consultant responsible for the IT systems that Chase uses, says: “All clients’ data is stored securely at iomart’s data centre and because no data is stored on the laptops the regional managers are using, they don’t have to be encrypted.” As a result of moving to the cloud, Chase Solutions says the management team now has much better control and visibility of its IT system. “It means that when Chase responds to a tender for work we can now tick every box with regards to security,” Mr Riley concludes.


CASE STUDY: CHASE SOLUTIONS ARE SECURE ‘THIN’ CLIENTS

