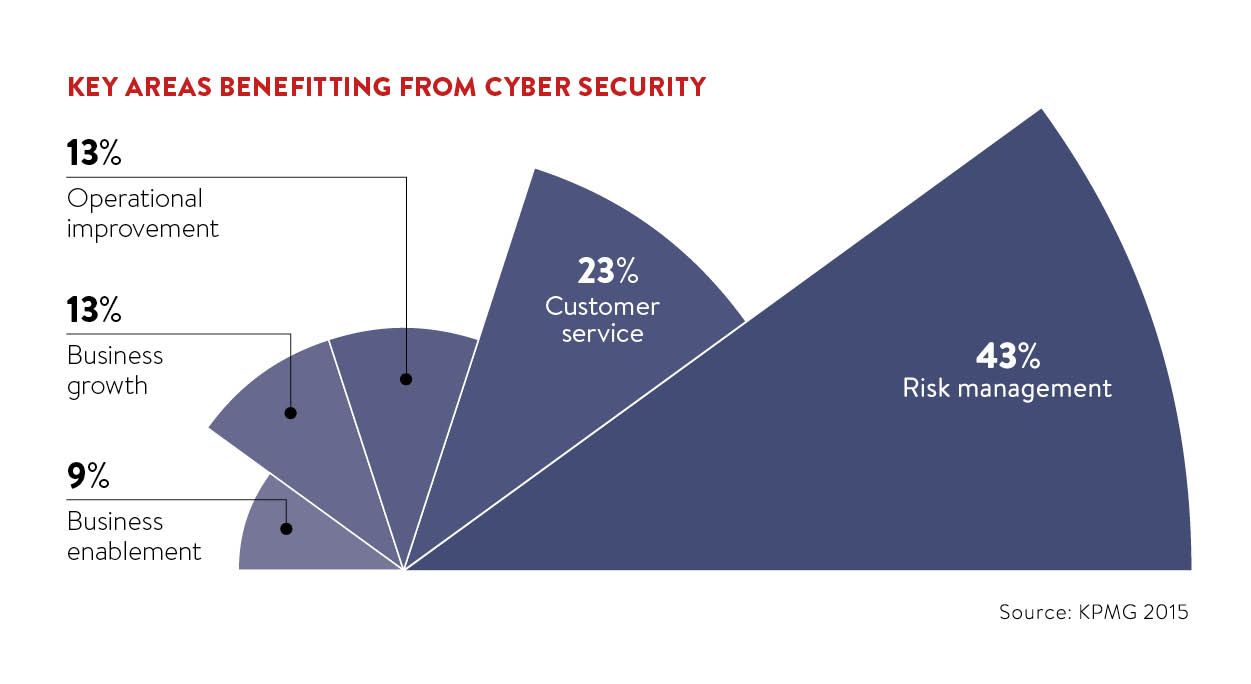
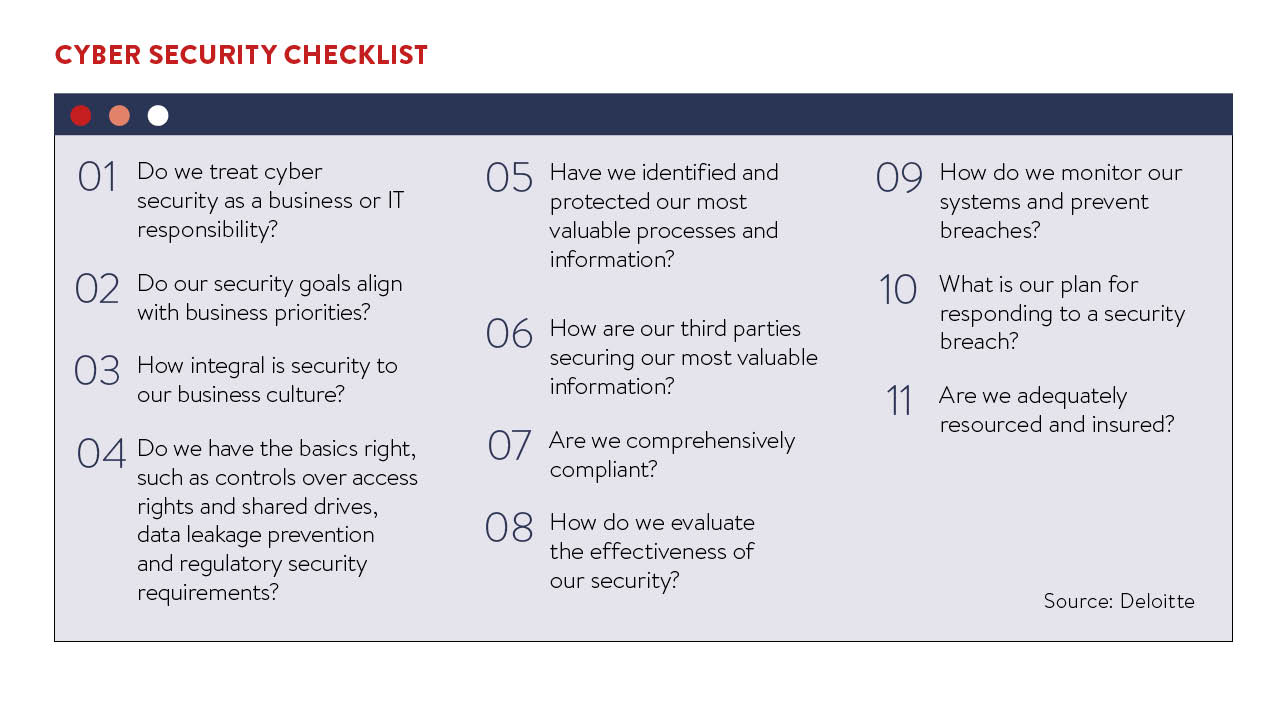
Accepting that data, be it the intellectual property a business is built on or the personally identifiable information held on behalf of customers, forms an integral part of the company from a strategic viewpoint is not optional. With threats growing both in volume and sophistication, the chief information officer (CIO) now has a truly pivotal role in the success of any business.
The trouble with examining the cyber threat-scape and attempting to draw lessons from attack examples is that it tends to be one-way traffic: there’s plenty of post-breach analysis, but precious little information from organisations that have successfully fought off an attack. We the media are partly responsible as “man didn’t bite dog” is hardly a news story and organisations don’t routinely reveal details of unsuccessful attacks as they are too plentiful. When they do, however, there are lessons to be learnt.
Analysing near misses
As Catalin Cosoi, chief security strategist at Bitdefender, points out: “Every security incident teaches CIOs a number of lessons that can be applied inside their company.” Most breaches remind CIOs to enhance their businesses security through traditional security practices, but what about those near misses?
“The difference between disaster and averted disaster is not the breach itself, but the preparation and response,” insists Ian Trump, security lead at LOGICnow. What matters is how quickly the breach is detected, the protection that has been put into place to prevent access to the most sensitive data and the public response. “CIOs need to lead the way out of the crisis,” says Mr Trump, “provide remedies and show what has been put in place to prevent this happening again.”
The importance of transparency, especially with customers post-breach, cannot be over-emphasised. Security group Kaspersky Lab knows all about this, as principal security researcher David Emm admits. Last year Kaspersky Lab detected a cyber-intrusion that impacted several of its internal systems.
“Kaspersky Lab addressed the issue in an open manner,” says Mr Emm, “exposing the attacker, and revealing other targets in a meticulously managed, transparent and responsible
communications strategy.” This meant taking appropriate steps to address the incident and prevent a similar breach from reoccurring, but also ensuring customers didn’t lose confidence in the organisation by communicating that their data and personal information was secure.
CIOs need to lead the way out of the crisis, provide remedies and show what has been put in place to prevent this happening again
Mike Cook, CIO at global software company PCA Predict, has also been there and done that. At the end of last year, PCA Predict was targeted by a botnet [robot network] which sent in excess of a million e-mails purporting to be from the organisation and “confirming” a payment of £120. The payload being a malicious attachment with a version of Dridex, designed to steal banking credentials from the recipient.
“We processed 60 times our daily call volumes in two hours from concerned members of the public,” Mr Cook reveals. “This required every single person in the business answering the phones and images contained within the e-mail were modified to read ‘This is spam’ to assist unaware recipients not to open the attachment they were sent.” As CIO, Mr Cook learnt you cannot rely upon IT to solve every issue and that people are your greatest asset.
Attacks with enormous impact
Then there are the lessons that can be learnt from those “Oh my goodness” security moments; moments such as the TalkTalk breach last year when data regarding at least 150,000 people was stolen and an estimated £60 million of damage caused to the company. It qualifies for OMG status because it was carried out by teenagers using a SQL injection attack, one of the oldest tricks in the application security book and which has been top of the AppSec threat pops for the last decade.
“It is quite disturbing that leakage with such an enormous impact is the result of an attack which is effectively mitigated by web-application firewalls,” says Itsik Mantin, director of security research at Imperva, in the understatement of the year.
And talking of lessons not learnt, how many more stolen credential attacks does there have to be before the dual dangers of credential theft and privilege escalation are taken seriously?
“The attack on Target revealed how easy it is to get into a large network if you have just one stolen credential,” Jonathan Sander, vice president of product strategy at Lieberman Software, insists. “What CIOs need to understand is that the old days of security being a wall you build around your soft, inner network are completely gone.
“The internet isn’t out there, it’s on every phone, every tablet, wiggling in with every cloud service and part of every operation your organisation does.” In other words, you can’t build a wall high enough when the needs of business users drag the attack vectors into every corner of the network.
Divestiture
Neither can you divest security responsibility, and not expect it to come back and bite you. Tyson Macaulay, chief security strategist at Fortinet, warns about divestiture when he says: “There is a trend towards partially divesting the CIO of responsibility for cyber security, because so much of it is leaving their control.”
Indeed, with shadow IT – solutions specified and deployed by departments other than the IT department – being procured by business lines ad hoc and launching online with their own budgets, the CIO is sometimes not consulted until it is too late, if at all.
Mr Macaulay has seen CIOs becoming frustrated at their rapidly globalising companies where shadow services are being developed without appropriate design considerations around security, yet the operational headaches are dropped on their heads to manage regardless.
It is vital, therefore, that the CIO operates at board level, but just as vital the CIO is capable of getting the right message across. “If the CIO can’t translate the language of technology to business,” says Andrew Rogoyski, vice-president of cyber security services at CGI, “they shouldn’t be in the post.”
Indeed, with boards asking more from CIOs by way of providing relevant security-related metrics and outlined business risks than ever before, that’s pretty much a given.
“CIOs are now having to gain an industry vertical-specific, threat-based perspective and learn the behaviours of certain adversaries to protect their information assets,” concludes FireMon chief information security officer Mark Carney. “CIOs are shifting their focus on cyber resiliency to ensure continued business operations, as the sophistication of hackers is increasing in nature.”
Analysing near misses

Attacks with enormous impact

