When the BYOD or bring-your-own-device trend first emerged, it was hailed by many technology experts as a game-changer for productivity, work-life balance and collaboration in businesses across all sizes and industries. Unfortunately, the reality has been markedly different, as a myriad of unforeseen issues has caused chief information officers (CIOs) to rethink their approach.
The first generation of BYOD policies left much to be desired and caused significant unease among employees, with technology research firm Gartner predicting in early-2014 that within two years one-fifth of all BYOD projects would fail.
“Companies instituted policies that were too stringent, so employees became afraid to adopt BYOD or had complaints after doing so,” says Nick Galea, chief executive of unified communications provider 3CX. “Many companies also failed to reassure employees that their personal information on their own devices would not be accessed by the company.”
While these oversights had high costs for some enterprises, there are crucial lessons to be learnt from their missteps, especially when the next generation of BYOD policies is considered.
Click here for the full infographic
Lessons to be learned
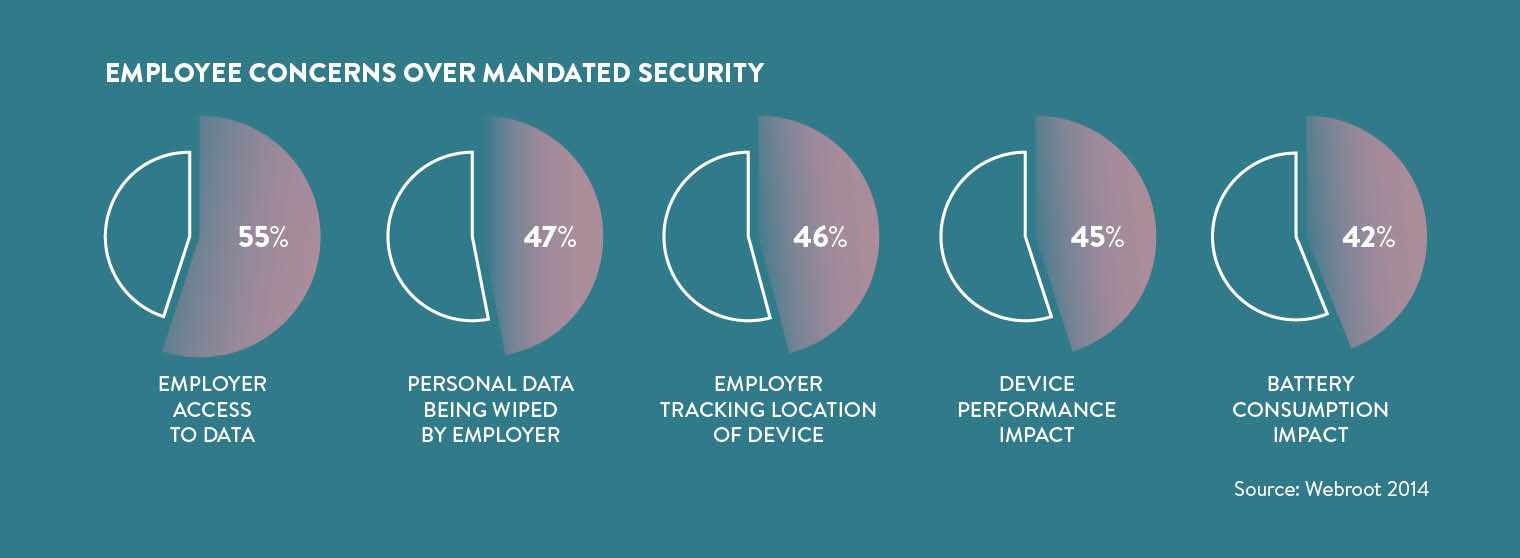
A central feature of many initial policies was strict containerisation, where users were only allowed to use a suite of select business apps, separated from the rest of the device. If this practice was followed in all respects then business data would be highly secure, but users have been largely resistant to this method, according to John Shaw, vice president of product management at IT security firm Sophos. “Having to sign in and out of two logically distinct interfaces, and being unable to use their favourite apps for work didn’t sit well with users in general,” he says.
The introduction of all-encompassing mobile device management (MDM) proved to be similarly problematic. This solution gives IT departments the ability to wipe the entire device clean, including all personal files, in the event of loss or hacking. Beyond the costly investment required to implement the system, MDM has security limitations that mean it is not a feasible option for most enterprises.
“Once my kids are logged on to play their favourite game on my iPad, they can send e-mails to anybody in my company contact list, including my boss. And the same goes for anybody who might happen to find my device on the train,” says Mr Shaw.
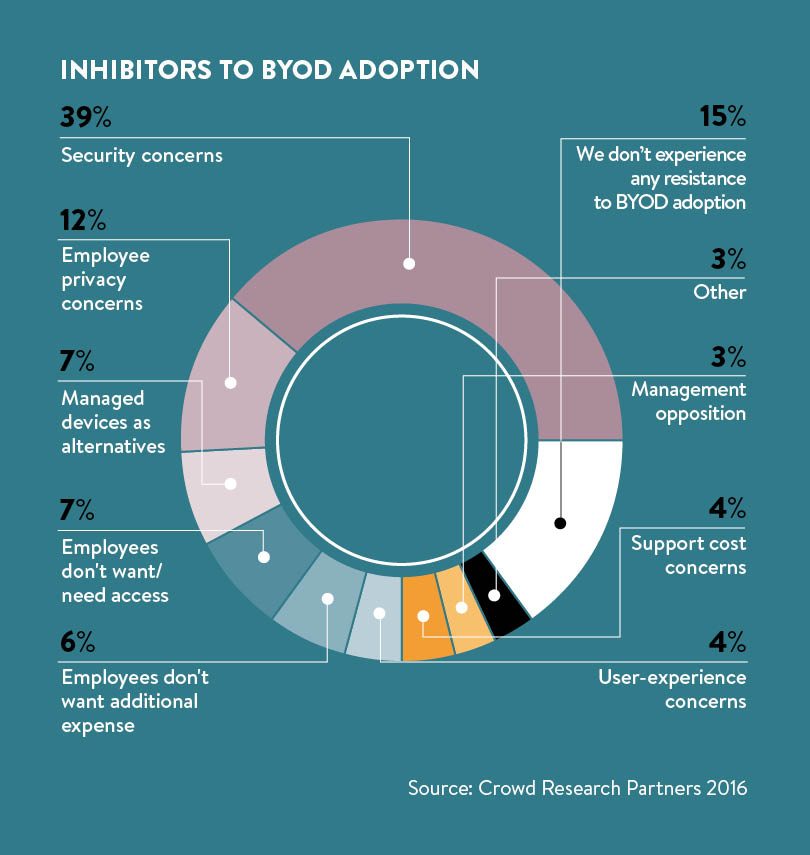
Some organisations may be hesitant to put BYOD policies into effect, viewing the potential security challenges as too much of a risk, but it’s now too late to put the genie back in the bottle, with a study commissioned by VMware showing that 39 per cent of UK employees would consider leaving their jobs if they were not allowed to use their mobile devices for work. Instead of looking for ways to fight against BYOD, enterprises need to embrace this movement and work with employees to ensure it is safely implemented.
“Employees are all working on personal devices. The devices may belong to the employee or to the company, but either way they are personal,” says Mr Shaw. “So BYOD has happened to some degree to every organisation; the only questions are how much control does IT have over BYOD and how wide open is the company’s security posture as a result?”
Just because a company forbids employees from downloading unapproved apps by blacklisting masses of popular programs doesn’t mean that issues of BYOD security will instantly disappear and in many cases employees will simply circumvent IT regulations. Almost 70 per cent of 20 and 30-something millennials openly admit to breaching IT policies and using apps not sanctioned by their employer, according to a survey conducted by TrackVia.
Even more concerning is the finding in the same study that 60 per cent of millennials, often referred to as digital natives, don’t have concerns about corporate security when they use unauthorised personal apps. “By all means, organisations should embrace #GenMobile’s penchant for openness, innovation and collaboration, using any device they wish, but only when they can understand and plan for the security risks these behaviours bring along,” says Alain Carpentier, Europe, Middle East and Africa vice president and general manager for Aruba, an HP Enterprise company.
Securing devices
The security considerations for BYOD are wideranging, but the fundamental goal is to assure the protection of corporate data held on employee-owned devices. Laptops, tablets and other devices owned by the company generally have a number of security safeguards in the event of loss or theft. Staff-owned smartphones lack these extensive protections, leaving them vulnerable to attack.
Storing critical business data with strong encryption on personal devices is clearly not a new development, but as the potential avenues for data theft grow, more precautions have to be put into practice. According to Mr Galea, the first consideration for an improved BYOD security policy is user authorisation. “Smartphones and tablets must be registered before they connect to the company network, and robust authentication procedures for users should be set up,” he says.
New mobile devices and apps are entering the market on a daily basis, bringing along with them unfamiliar software and new vulnerabilities. For that reason, a static BYOD policy is doomed to fail. “It is important to review existing policies and modify them to meet the changing business needs, rather than trying to defend why old policies and practices should translate to new mobility challenges.” says Ali Neil, head of security services for Verizon in Europe, the Middle East and Africa.
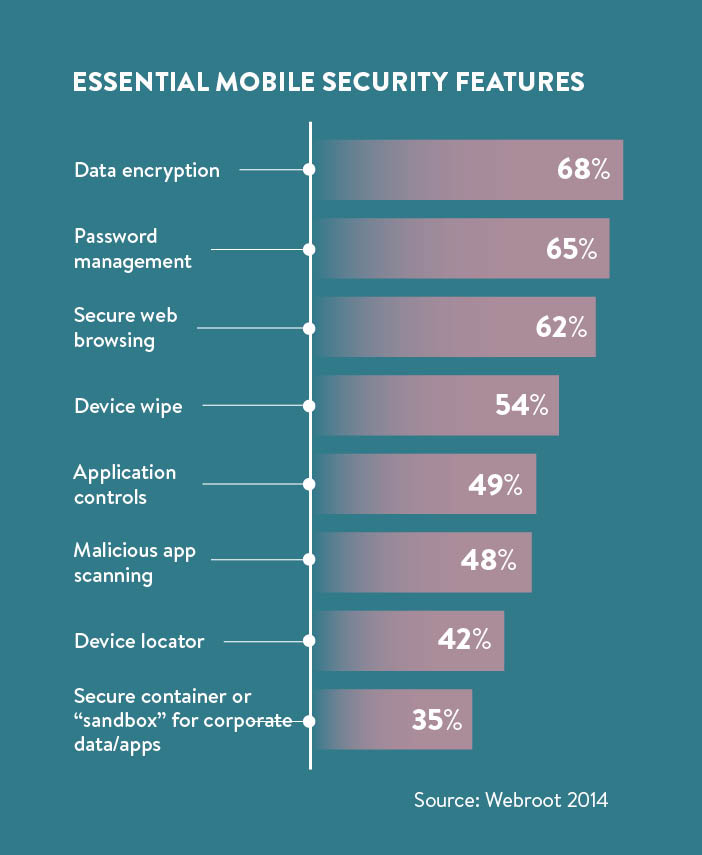
There is no one-size-fits-all solution for BYOD. Each organisation’s policy evaluation should be carried out under a framework that comprehensively assesses risks and challenges faced by the company. Moving beyond the initial mobile security analysis, using a specialised third-party testing service on a regular basis can help get a fresh perspective on protection issues and cover any corporate IT blind spots.
Although CIOs and IT departments will be responsible for creating successful BYOD policies, employees themselves need to play a central role in their implementation. No matter how comprehensive and scalable an enterprise’s BYOD policy may be, unless staff fully understand the policy itself and the risks associated with their devices at work, there will still be major security dangers.
Beyond the basics
Employees’ responsibilities in successful BYOD policies go beyond simply using strong passwords and changing them regularly. For example, users should make sure apps are kept up to date and not be careless when accessing important business data outside the workplace. Research from Acronis revealed that 77 per cent of employees globally had not undergone any education around the threats associated with BYOD.
Many first-generation BYOD schemes didn’t succeed partly due to resistance from employees, who just utilised unauthorised apps, but also because IT departments found policies to be overly complicated and impractical. Making BYOD as easy as possible to set up and maintain is key for CIOs, who need to consider the often overworked IT workers, as these tech professionals will be the ones involved in the day-to-day managing of BYOD policies.
The higher-than-expected costs from BYOD app security, policy management, system infrastructure and regulatory compliance from past deployments can now be more accurately projected by companies, so processes can be streamlined to bring in cost-savings.
Enterprises can still realise the benefits of BYOD, from reduced costs, improved activity and increased employee satisfaction, if equilibrium between scalability and usability is reached. “The lesson is to find a balance between the two approaches in a way that is largely invisible to users,” says Mr Shaw.
An example of how this could be achieved is by ensuring company data and personal information remain isolated from each other at all times, through individual app separation. The selected wiping of sensitive corporate data should also be allowed, while not erasing personal messages, e-mails and apps.
Businesses can no longer ignore the growing BYOD movement. “Failure to support BYOD will impact productivity and will reduce employee satisfaction,” Mark Ebden, strategic consultant at IT services firm Trustmarque, concludes. While recognising security of corporate data is a major concern for CIOs, “companies must make use of the tools available to them to manage BYOD – to ensure BYOD functions effectively as a sensible policy, but at the same time does not impact on the usability of devices”, he says.
FEELING COMFORTABLE WITH USEFUL WEARABLES AT WORK

From the much publicised launch of the Apple Watch to fitness trackers such as Fitbit, wearable technology has rapidly become commonplace in a matter of just a few years. Researchers at analysis and advisory firm IDC forecast the global wearables market would ship 72 million units in 2015, a year-on-year growth of more than 173 per cent. However, the relative simplicity of wearables’ applications in the workplace means that, at the moment, their presence at work has been minimal.
“Without voice or video, there’s less reason to integrate them with other communications,” says Nick Galea, chief executive of unified communications provider 3CX. This is expected to change with the increasing popularity of wearables, which will further propel these devices into the mainstream. “As product and software developers begin to add apps and features that support unified communications and encourage use in the workplace, we’ll see much more complexity,” adds Mr Galea.
Enterprises need to begin planning now for the widespread usage of wearables, as many current IT infrastructures are drastically underprepared for the incorporation of these devices. Mark Ebden, strategic consultant at IT services firm Trustmarque, believes it will be hard to customise wearables to satisfy the complex demands of mobile enterprises, due to proprietary technology which the majority of devices are based on.
Wearables have the potential to alter the mobile enterprise security landscape in ways not experienced before. “In particular, the fact wearables are generally broadcasting and listening, using Bluetooth, is a rising concern to security teams,” says Mr Ebden. Google Glass is a prime example of the challenges wearables can create, as smartglasses have the ability to record sensitive company data without the need to even be on the same network.
A Symantec report found that 20 per cent of login credentials sent by wearables are not encrypted, giving cybercriminals open access to user-sensitive IDs and passwords. Unless comprehensive and dynamic BYOD policies are phased in that cover wearables, then corporate data will remain at risk.
Lessons to be learned

Securing devices

