The rise of machines is upon us, fronted not by killer robots from the future, but by hopelessly insecure webcams. Last month millions were left unable to access many of the most frequented websites after insecure internet of things (IoT) devices were commandeered to assault a key online pressure point.
Hackers hijacked an estimated 100,000 internet-connected devices by taking advantage of default, factory-set passwords before using these devices as a platform to flood Dyn, a US-based supplier of managed DNS (domain name system) services, with junk traffic.
By rendering Dyn inoperable, hackers effectively obscured the “road signs” that allow surfers to navigate the web. Many high-profile sites, including Amazon, Twitter, Reddit, Netflix and more, become inaccessible during a wave of attacks on October 21.
The details
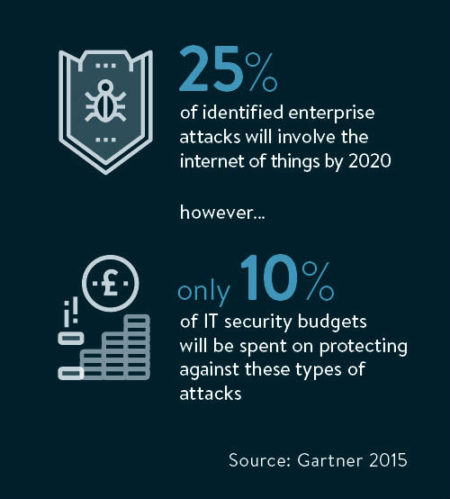 These attacks against a key internet technology were run using a botnet – a zombie network of compromised devices – made up of compromised routers, digital video recorders, webcams and security cameras. Hackers used a strain of malware or malicious code called mirai (Japanese for “the future”) to infect and control these IoT devices.
These attacks against a key internet technology were run using a botnet – a zombie network of compromised devices – made up of compromised routers, digital video recorders, webcams and security cameras. Hackers used a strain of malware or malicious code called mirai (Japanese for “the future”) to infect and control these IoT devices.
A group called New World Hackers, earlier linked to an attack that knocked out the BBC’s iPlayer last New Year’s Eve, claimed responsibility for the assault.
The mirai malware had also been linked to separate, less high-profile distributed denial of service (DDoS) attacks against cyber-crime blogger Brian Krebs and French hosting provider OVH in mid-September. Source code for the malware leaked online in early-October, giving copycat hackers a blueprint to create botnets of their own.
Although mirai seems solely focused around DDoS, it would be possible to use compromised routers to redirect users to phishing sites or to allow the attacker to steal data from internal network shares.
The scale of the attack has caught the attention of politicians. Chancellor Philip Hammond referred to “worrying expansion in the scale of DDoS attacks” during a speech announcing a revamp of the UK’s National Cyber Security Strategy at the start of November 2016.
Mr Hammond referred to attacks that take advantage of “insecure coding, weak access controls, poorly implemented cryptography and unprotected databases”.
Security experts have long warned that security mistakes made and resolved in the field of computer and mobile devices years ago are being repeated in the development of internet-connected devices, which often rely on embedded processors running the Linux open source operating system.
IoT in the office
Although most familiar in the home, IoT devices ranging from connected light bulbs to building management systems are attractive to business because they offer cost-savings.
Ken Munro, a director at UK security consultancy Pen Test Partners, says the list of vulnerable IoT equipment in small business is long and growing. These include CCTV security cameras, creating a back door into the network, building alarms that can be hacked and switched off over radio frequencies, as well vulnerable smart coffee machines, thermostats, building management systems and more.
Many devices are not designed to be updated. Even if updates exist, notification is rare, so even conscientious users will be left in the dark, assuming they’d take the trouble to patch their systems.
“The most dangerous IoT devices out there are the ones that don’t have a decent patch pipeline or upgrade path,” says Tod Beardsley, senior research manager at Rapid7, the firm behind the popular Metasploit penetration testing tool. “That’s the crux of everything here. Not so much which devices, but it’s any device that can talk on the internet and can’t or won’t be patched.”
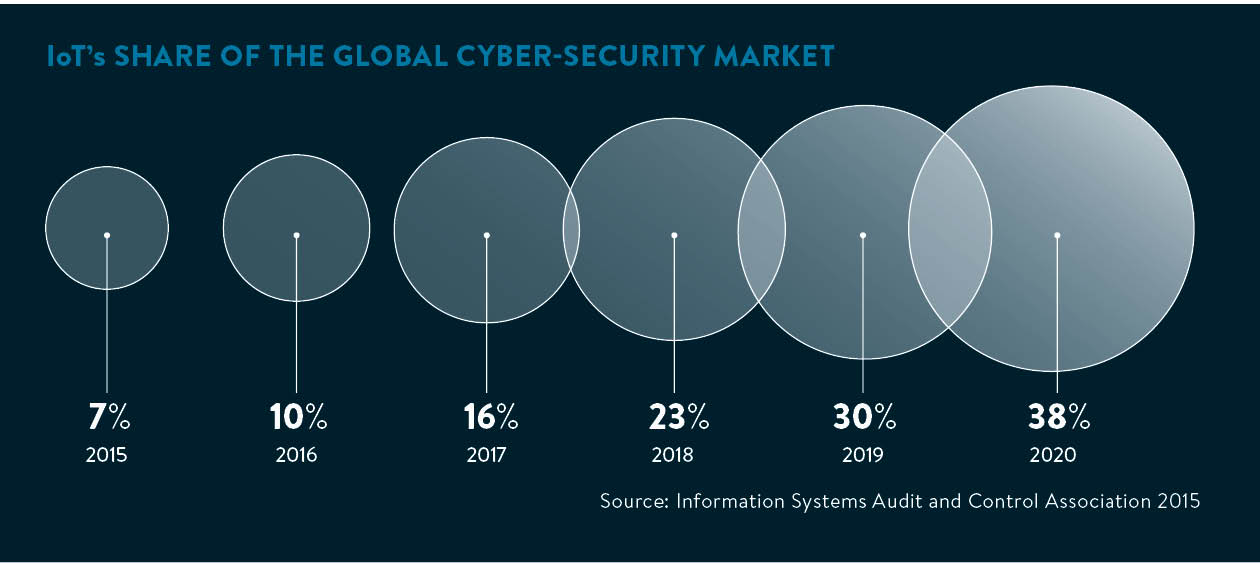
Daniel Miessler, director of advisory services at IOActive, says the IoT risk to business centres on rolling out products, connected to other business and operational technology systems.
Protecting IoT systems involves understanding what they are, how they connect and what their capabilities are, Mr Miessler explains.
“Many IoT systems have a local web server, a mobile application, listening network ports, and cloud connectivity,” he says. “Using them normally often involves dozens of connections to third parties, so it’s important to know what are those dozens of connections? What data is being sent? Are there ways to control the device remotely? What credentials and access methods are used to protect each part of this ecosystem?”
Retailers ought to be concerned about a repeat attack on their sites during late-November and early-December, traditionally the busiest shopping periods of the year
The business landscape is yet to adjust to IoT vulnerabilities. “Businesses are just starting to realise both the promise and the risk of IoT,” says Mr Miessler. “Some companies are being cautious and careful, but many are embracing the functionality enthusiastically and placing themselves in danger in the process.
“Right now businesses, like the industry as a whole, are largely in a wait-and-see mode where they’re not sure how and when to deploy IoT, when so many of the risks seem both unknown and substantial.”
Protecting your business
Some defences against abuse and attack are already possible. For both businesses and security-conscious consumers, a number of straightforward defences can be applied. Changing from the default password on any purchased equipment is a must. In addition, users should turn off port-forwarding and UPnP (universal plug and play, a home networking protocol) on their routers. Finally businesses should segment their network so that a compromised device on any segment can’t be used to access more sensitive resources such as e-mail and company file servers.
US cryptographer Bruce Schneier recently warned that the market won’t be able to resolve the IoT security problem because neither the buyer nor the seller cares about the problems caused by insecure IoT technology. Chinese manufacturing company Hangzhou Xiongmai recalled several models of webcams that were hijacked by mirai malware. But the recall falls short of evidence that vendors can be forced to act through market pressure, according to Mr Schneier.
“Vendors can choose to act, but they can’t be forced to act,” he says. “That’s one electronics firm out of many that are vulnerable. Recalls aren’t a long-term solution to a continually recurring problem. Imagine if Apple had to recall its iPhones every time it issued a security update.”
Sean Sullivan, a security adviser at anti-malware firm F-Secure, says retailers ought to be concerned about a repeat attack on their sites during late-November and early-December, traditionally the busiest shopping periods of the year.
“If any DDoS attacks do disrupt retail or other notable attacks occur, there will be calls to regulate IoT devices, demanding better security and passwords by default, while largely ignoring that a great deal of network operator infrastructure could be improved to reduce its vulnerabilities to reflection attacks,” Mr Sullivan says. “IoT devices would not be as dangerous if many networks were configured properly.”
Cees Links, a general manager of Qorvo, provider of low-power, low-cost radio-frequency communication technology for the IoT, is optimistic that security challenges can be overcome.
“History shows that security is a learning process,” he says. “Every day, we are learning what the risks are, but this will take time and, unfortunately, it will take some victims as well. There is a sense of urgency, and I know there is a lot of work done making the IoT a safe and secure place.”
Asked whether a market-based solution to this IoT insecurity problem was possible or whether government regulation was needed, Mr Links, who led the team at US networking firm Lucent that invented and popularised wi-fi technology, conceded that government may have a role to play. “Government needs to make laws and enforce them,” he says.
Government involvement in setting standards for IoT security is so far preliminary. A one-day meeting convened by the US Department of Commerce in mid-October, for example, proposed a new labelling system for smart home devices. This may take years to come to fruition.
Consumers and small businesses buying electronic equipment can look for the CE mark for reassurance that the device satisfies the requirement of applicable European directives, such as electrical safety, but there’s no information security equivalent. In the meantime, IoT device manufacturers are continuing to supply equipment marketed solely on price and functionality. The market has not yet matured to the point buyers will pay more for a more secure device, and there’s no clear yardstick to judge between secure and less-secure products anyway.
IOActive’s Mr Miessler struck a downbeat note typical of other security experts. “IoT security is going to get a whole lot worse before it gets better,” he concludes.
The details

IoT in the office

