Exploitation of privilege and authentication is evident in nearly every major ransomware attack or data breach, costing hundreds of millions of pounds in business disruption and reputational damage. These attacks have been on the rise for years and continue to grow at pace, and yet most organisations are not prepared.
Attacks on Kerberos, the default authentication protocol for domain-controlled devices on Windows, are particularly common among cybersecurity incidents. Attackers will frequently leverage limitations in Kerberos and Microsoft Active Directory, the underlying application that supports who can do what to whom on most enterprise networks, to forge false Kerberos tickets capable of granting them administrative privileges.
Detection of these forgeries in post-attack forensic analyses is often impossible because standard logging of enterprise domain controllers and Active Directory doesn’t see or capture the necessary data.
This is a vast problem considering nearly all the world’s large corporations, including 95 per cent of Fortune 500 companies, run on Active Directory. All enterprise security is premised on authentication working correctly and that users are who they say they are, yet Kerberos attacks are simple to carry out with open-source tools, such as Mimikatz and Rubeus, which are now freely available on GitHub and allow hackers to impersonate internal users with illegitimate but accepted credentials. All the logs in the system will say it’s a legitimate user taking an action, even when it’s not.
In the current decentralised work environment, where so many employees access resources remotely, addressing authentication is a challenge every business should be prioritising. But it must be done correctly if they are to avoid falling victim to data breaches or ransomware attacks. A company that can’t ensure users are who they say they are will have a hard time knowing the right people are doing the right things on its computing network. 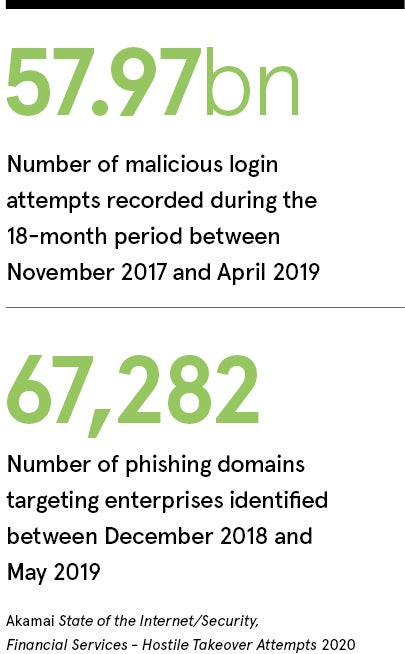
Consequences of not taking appropriate measures to detect and stop attacks against authentication infrastructure can be catastrophic and multi-factor authentication, while helpful elsewhere, is powerless against this phase of the attacks.
“The thorny underbelly of authentication is that every single system in the enterprise, from a security perspective and from a business perspective, assumes you are who you say you are,” says Jason Crabtree, co-founder and chief executive of QOMPLX. “At this point, that’s a really dumb assumption because protocols like NTLM, Kerberos and SAML can all be manipulated to allow hackers to not be who they say they are.
“The only way to catch this is to diligently work to disable legacy protocols like NTLM and buy either Microsoft ATA/ATP or a more comprehensive and effective tool set from QOMPLX for monitoring and validating Kerberos. Only QOMPLX takes the details of every Kerberos interaction and keeps a stateful ledger to track that every presented credential is duly issued and presented in near real time, massively improving detection accuracy.”
QOMPLX can validate every single Kerberos transaction across global enterprises and its attack detection techniques remain valid regardless of which tool is used to forge a ticket. Its cybersecurity decision platform Q:CYBER is the only analytic framework able to detect the most devastating attacks in near real time, without false positives and with high confidence using targeted model-based detections.
“A huge number of organisations are in a position where they have tremendously expensive security programmes that basically don’t matter as they are based on unreliable data,” says Crabtree. “If they aren’t doing this real-time validation of authentication events, then downstream applications and detections can’t operate correctly.
“With five years of tremendous investment and effort, we’re the only company in the world that keeps track of every authentication event in order and at scale. Unless you do that, you don’t know if one of those events is forged. Authentication is security control number one. Everything else can follow. If you get that wrong, it’s very difficult to recover later because everything assumes it must be true. It’s like missing gravity.”
For more information please visit qomplx.com





