
For former office-based staff, working all or part of their time from home is ever more clearly a permanent shift. New research shows that more than eight in 10 staff have increased their work from home since the start of the coronavirus pandemic, and many expect this high level of home working to remain in place.
While many organisations have benefited from the increased productivity and employee satisfaction of remote working, the setup also presents significant new cyber security threats. As employees mix and match work and personal phones or laptops - using non-secure personal devices, including printers, to access corporate systems - a raft of new security risks are introduced.
Seven in 10 office workers now use business devices for personal tasks, increasing the risk of malware on systems that access sensitive corporate data. The research, commissioned by HP Wolf Security, shows that a third of employees also share corporate laptops and phones with their families and friends.
Meanwhile, some 69% of staff often use their own laptops or printers to carry out work tasks, commonly accessing sensitive customer, operational, financial and human resources data, on devices that may be insecure or already infected.
Blurred lines
Since the arrival of the pandemic, the distinction between professional and personal lives on an average day has become less clear, according to more than three quarters of the nearly 8,500 office workers surveyed. Half describe their work tools as personal devices, which is understandable in flexible work contexts but also presents profound corporate risk.
“With employees working remotely, the lines between work and personal equipment are blurred, and everyday actions, such as opening an attachment, can have serious consequences,” explains Joanna Burkey, chief information security officer at HP. “Without all of the pre-pandemic sources of visibility of devices, including how they are being used and by whom, IT and security teams are working with clouded vision.”
All of this presents major problems as sophisticated malicious actors quickly adapt to the new environment by exploiting gaming platforms, mimicking popular streaming services and emailing malware-infected files to personal accounts to gain access to home networks and to slip through corporate defences.
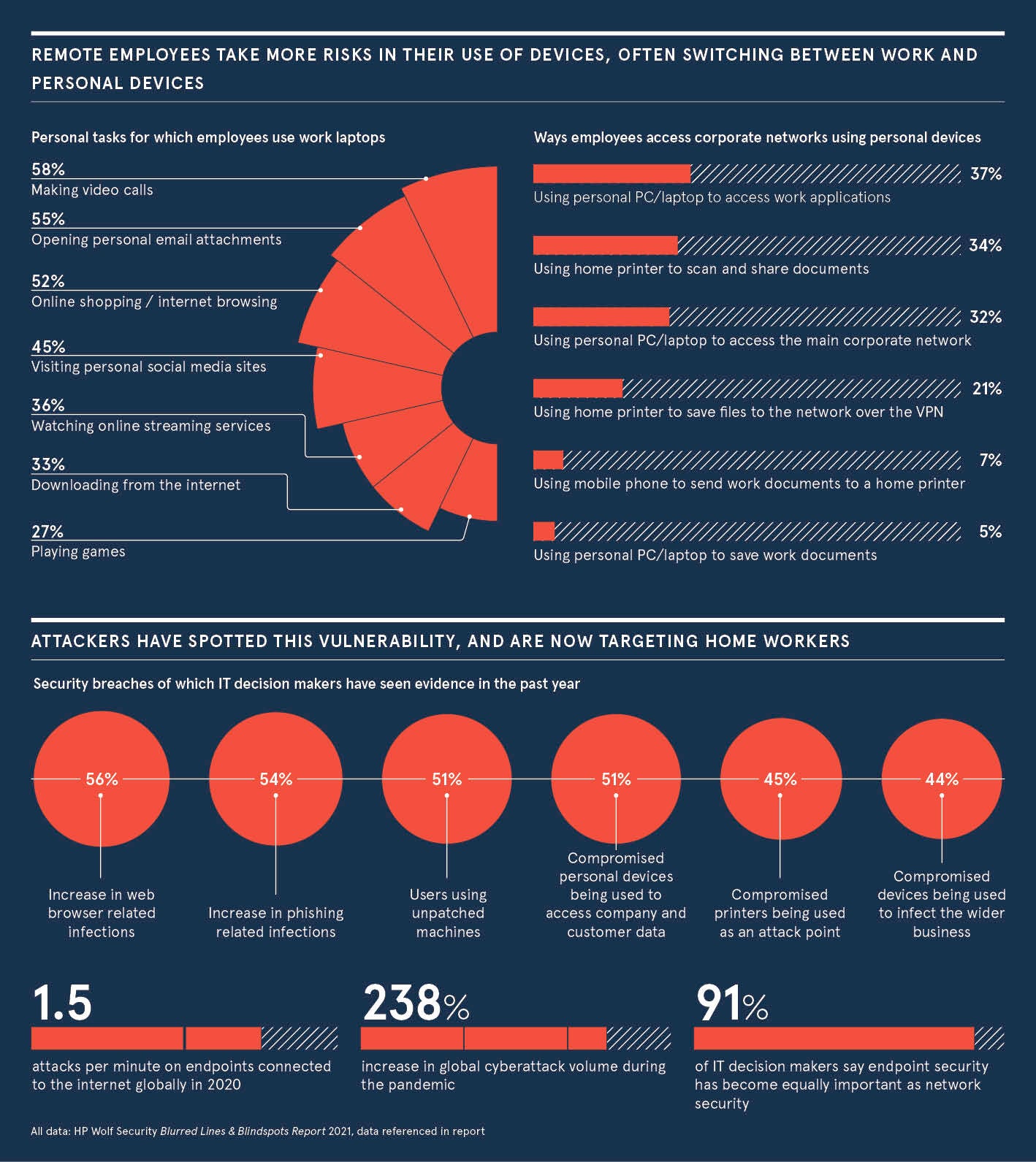
Businesses are beginning to witness the impacts. “In the past year, more than half of IT decision-makers have seen evidence in their company of compromised personal PCs being used to access company and customer data. This is a huge risk that could lead to exposed company data, reputational damage, non-compliance and loss of customer trust,” warns David Prezzano, UK and Ireland managing director at HP.
As employees take more risks, a surge in email phishing attacks and web browser download infections means 44% of 1,100 decision-makers interviewed have witnessed compromised devices infecting their wider businesses. Research firm KuppingerCole highlights a 238% increase in cyberattacks during the pandemic, with employees’ connected devices contributing to a breakdown of the traditional corporate IT infrastructure and network. Clearly, hackers are taking advantage of the new setup.
Outdated security
Typically, businesses are stuck in an old approach to data security, allowing the problem to grow. Their methodology originates from an era of traditional network perimeter protection and firewalls, despite the establishment of a dispersed workforce and cloud computing. When a breach happens, it often remains completely invisible until after serious harm has occurred.
“The traditional ways of securing access to the corporate network, applications and data are no longer fit for purpose, and the concept of a perimeter has become obsolete,” explains Dr Ian Pratt, global head of security, HP Personal Systems. “Critical data is being hosted outside the enterprise firewall. The time has come for organisations to start taking a proactive approach to security, architecting their infrastructure to be resilient to attacks.”
Users are the point of entry for most attacks and that’s why endpoints account for 70% of successful breaches
In this environment, heads of IT cannot view the shift to home working as a one-off event and they cannot lock down all devices. The pandemic has changed the way people operate and organisations need to reassess how they manage the new risks. They must, however, do so without harming workforce mobility or jeopardising productivity.
A new approach
The growing demands on IT infrastructure have increased the focus on endpoints, including mobile phones, tablets, laptops and even connected printers, so that threats can be tackled sooner. As organisations become ‘perimeter-less’, nine in 10 IT leaders say getting endpoint security right is now as important as having strong network security.
“Users are the point of entry for most attacks and that’s why endpoints account for 70% of successful breaches, with malware almost always being delivered via email attachments, web links and downloadable files,” says Pratt. “Phishing is of particular concern, with attackers using new techniques including AI-automation and personalisation.”
Evolving security dangers demand more robust defences. Companies are increasingly using HP Wolf Security, a new breed of endpoint security. The portfolio includes the world’s most secure PCs and printers*, hardware-enforced endpoint security software and advanced services, offering comprehensive cyber resilience that intelligently protects against the many emerging endpoint threats.
Using HP Wolf Security, organisations are taking a ‘zero trust’ approach, meaning every device is considered a potential threat and can be automatically protected. They are also taking advantage of self-healing firmware, in-memory breach detection, threat containment via virtualisation and cloud-based intelligence.
Given that the new world of remote work is here to stay, companies can no longer afford to remain focused on traditional network perimeters that miss the dispersed points where data is accessed. Smart endpoint security enables businesses to tackle evolving threats on myriad dispersed devices, while reducing operational impact and empowering flexible productivity. Getting this right is essential to the future of their operations.
To find out more about HP Wolf Security in the fast-changing remote working world, visit
www.hp.com/wolf
Disclaimer: PCs: Based on HP’s unique and comprehensive security capabilities at no additional cost among vendors on HP Elite PCs and HP Workstations with Windows and 8th Gen and higher Intel® processors or AMD Ryzen™ 4000 processors and higher; HP ProDesk 600 G6 with Intel® 10th Gen and higher processors; and HP ProBook 600 with AMD Ryzen™ 4000 or Intel® 11th Gen processors and higher.
Printers: Claim includes HP’s most advanced embedded security features which are available on HP Enterprise and HP Managed devices with HP FutureSmart firmware 4.5 or above. The claim is based on HP review of 2019 published features of competitive in-class printers. Only HP offers a combination of security features to automatically detect, stop, and recover from attacks with a self-healing reboot, in alignment with NIST SP 800-193 guidelines for device cyber resiliency.
HP Security is now HP Wolf Security. Security features vary by platform.
Promoted by HP

For former office-based staff, working all or part of their time from home is ever more clearly a permanent shift. New research shows that more than eight in 10 staff have increased their work from home since the start of the coronavirus pandemic, and many expect this high level of home working to remain in place.
While many organisations have benefited from the increased productivity and employee satisfaction of remote working, the setup also presents significant new cyber security threats. As employees mix and match work and personal phones or laptops - using non-secure personal devices, including printers, to access corporate systems - a raft of new security risks are introduced.
Seven in 10 office workers now use business devices for personal tasks, increasing the risk of malware on systems that access sensitive corporate data. The research, commissioned by HP Wolf Security, shows that a third of employees also share corporate laptops and phones with their families and friends.

