The cyber-threat landscape has continued to evolve drastically as hackers have sought to exploit new vulnerabilities emerging through the ever-widening use of technology by businesses and society.
Cybercriminals have matured their use of ransomware, conducting small-scale exploits to enable intensive reconnaissance before a full-on attack, and using multiple known vulnerabilities to breach systems.
Advanced persistent threats, meanwhile, have become more focused on accessing details about how production environments work and brand sabotage is increasingly inflicted by attacking the integrity of a supply chain to cause recalls and production slowdowns.
The growing frequency, velocity and potential damage of these kinds of attacks on organisations has driven the rapid ascent of the term “cyber-resilience” in the business vernacular. Yet while companies will now regularly express their desire to be cyber-resilient, there remains a lack of clarity and understanding around what that actually means and, most importantly, how it can be achieved and sustained over the long term.
“Understanding the definition is somewhat difficult for a lot of companies, as I experienced at a recent conference,” says Dirk Schrader, cyber-resilience architect and chief marketing officer at Greenbone Networks, a global provider of resilience and vulnerability management solutions.
“There were five panellists, including a government official and the chief information security officer of a large defence firm, discussing their take on cyber-resilience. I asked them about their definition of cyber-resilience and earned silence. They didn’t have one.”
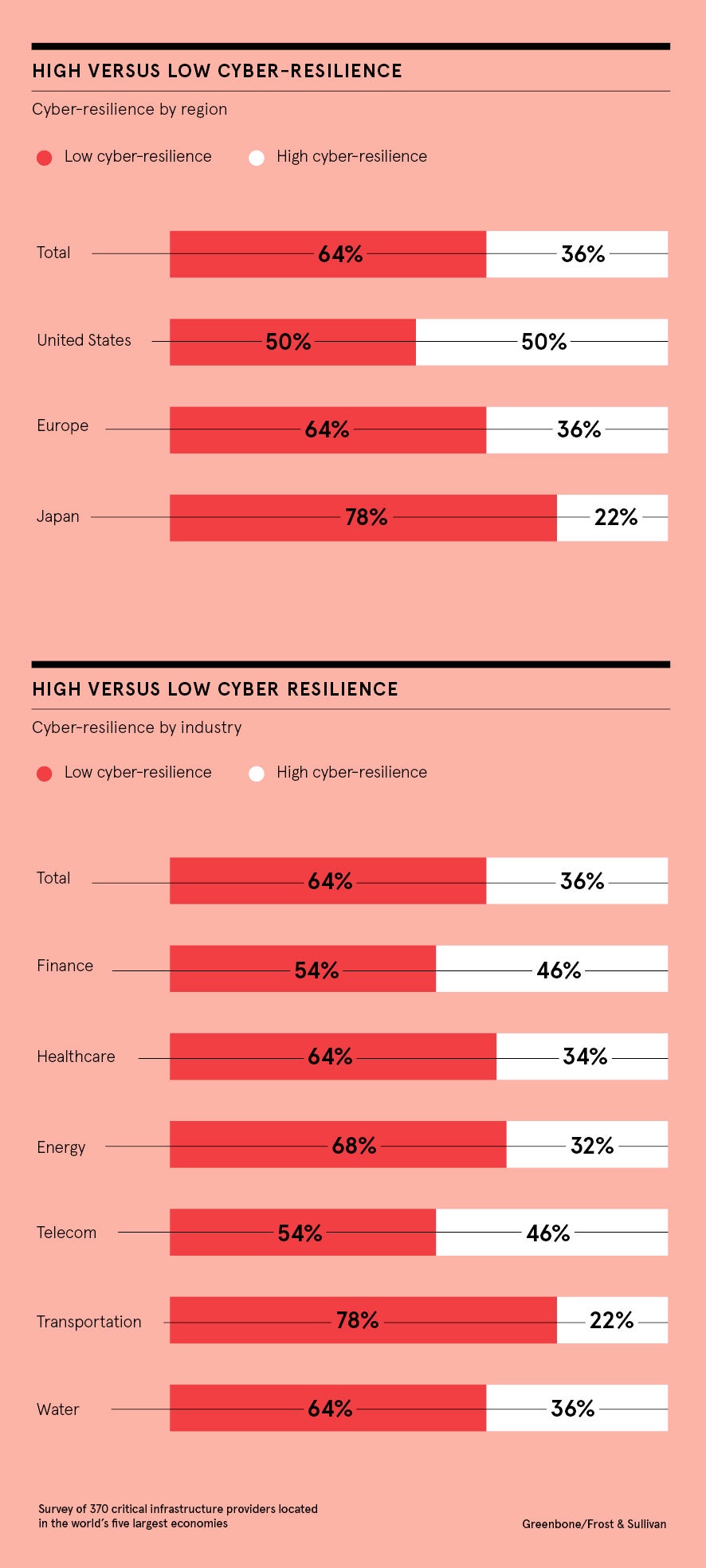
Such confusion could perhaps explain why genuine cyber-resilience capability is lacking across many industries. A study by Greenbone Networks and analyst firm Frost & Sullivan found only 36 per cent of organisations are what they deemed to be “highly cyber-resilient”. Though this is higher for regulated industries, such as financial services and telecoms, where 46 per cent of companies were found to be highly cyber-resilient, sectors like energy (32 per cent) and transportation (22 per cent) flounder behind.
Cyber-resilience is not a matter of budget, according to the research, but rather putting in place good business practices and establishing a thorough understanding of mission-critical digital assets and business processes for both information security and operations staff.
Being able to activate these teams quickly is one of the most significant distinctions between companies’ resilience levels. Of those found to be maintaining a higher level of cyber-resilience, 43 per cent primarily view it as a technology issue.
Greenbone’s understanding of cyber-resilience, shared by researchers from Stockholm University, focuses on an entity’s ability to continuously deliver its intended business outcomes despite adverse cyber-events.
The danger is simple: if the traditional approach to information security doesn’t change, it will be easy for cybercriminals to attack
The objective of cyber-resilience, they say, is to ensure business delivery, not just protect IT. Its intention is to enable failure in a safe and controlled way, as opposed to “fail safe”, which is often understood as no failure at any cost.
Its approach is to build security from within the business processes, rather than putting security fences around them. Its architecture is multi-layered, considering business-critical assets first and foremost. And its scope does not stop at the boundaries of a single organisation, but instead encompasses the interconnected nature of businesses, their supply chains and end-customer setups.
“If organisations are using digital assets to render services or provide products, they are dependent on these elements to deliver their intended business outcomes,” says Schrader.
“These intended outcomes and the businesses processes involved are the elements, from a business risk perspective, vulnerable to being interrupted if they have a cyber-event. The dependency on digital assets will continue to rise, making cyber-risk incidents a top peril for future growth. The danger is simple: if the traditional approach to information security doesn’t change, it will be easy for cybercriminals to attack.
“The existing, widely used concept of implementing security – a one-size-fits-all approach to firewalling and building high fences around the network – has been proven to fail. Cyber-resilience is the only way to overcome the disconnect between technical information security, such as firewalls and VPNs [virtual private networks], and high-level information security management systems being used in large organisations, as mandated by regulations.
“Cyber-resilience can’t be achieved with a high wall around your business processes. You need to really embed the resilience and digital hygiene into the business processes.”
Greenbone Networks delivers a vulnerability analysis solution for enterprise IT, which includes reporting and security change management. It helps companies to identify and measure the attack surface, model critical business processes and visualise them to see which have the largest risk and what would happen if a risk or vulnerability is exploited.
The Greenbone Security Manager, in its various forms, including OpenVAS, now known as GVM, is deployed in more than 30,000 installations and integrations across a broad range of industries and company sizes. It has been downloaded more than 2.5 million times.
The company advocates a three-step process to embedding cyber-resilience in business processes. In the first step, it’s crucial to be clear about business processes from the outset; how they stack up on and interact with each other, which ones are critical and what are the critical steps within them.
Organisations should ask themselves what would happen if certain attack surfaces appear and then have answers in place. By simulating these what-if scenarios, pre-empting attacks on critical assets and quickly implementing new processes or revising existing ones to recover rapidly from attacks, companies are twice as likely to be highly cyber-resilient.
In step two, organisations should make sure responsibilities are aligned when it comes to remediating and mitigating identified points of vulnerability. Business processes and cybersecurity architecture should also be aligned and it’s important they avoid gaps and unrealistic expectations in their organisational agility to respond quickly.
Companies with these capabilities are three times more likely to be highly cyber-resilient. If they can reach step three, however, that likelihood doubles. It means they are proactive if a process evolves or changes and they maintain communication with business process owners, visualising the risk for them in their own terminology.
“Building cyber-resilience is one thing, but it’s crucial to sustain that over time,” says Schrader. “As a business evolves, it will make changes to processes. It might have to adapt to new regulation or develop new products and services. The challenge is to embed cyber-resilience as a concept into each evolvement. Culture is one way to maintain and sustain cyber-resilience. The other element is more technical, connecting existing infosec technology through applying cyber-resilience into business processes.
“The future of business risk will be driven by players who are able to connect the currently distinct topics of business process and information security management at board level, and information security status and tooling in such a way that process changes can easily be visualised and managed, while a high level of cyber-resilience is maintained. Our aim at Greenbone Networks is to provide a tool to do exactly that.”
For more information please visit www.greenbone.net/en/businessrisk