In 2015, Adrian Leppard, then City of London police commissioner, made a striking statement: cybercrime had eclipsed the drugs trade in value to organised crime and the police did not have enough resources to tackle it. It’s not often a police commissioner’s comments make it into the business pages of newspapers, but it was clear organisations of all sizes shared his concerns and, unlike with the drugs trade, they were all potential targets.
Since then, the proliferation of organised crime and get-rich-quick merchants on the internet has accelerated even further, amplified by a global pandemic that has seen fraudsters prying on people working from home. According to Kroll, the corporate investigations and risk consulting firm, national lockdowns have caused ransomware to overtake business email compromise as the principal attack affecting companies.
“Part of this is because there is no business as usual and it is huge money that can be made relatively easily without fear of detection or being caught,” says Andrew Beckett, managing director and Europe, Middle East and Africa leader for Kroll’s cyber risk practice. ”IT estates are now distributed and it’s harder to monitor for companies that didn’t have strong monitoring in place beforehand. A lot of organisations are using out-of-date, unpatched VPNs and you’re not sitting next to a colleague who can just do a quick sanity check for you. ‘Does this look right to you?’ ‘Do you think I should do this?’ You don’t have that option anymore.
“The pandemic highlighted the flaws in existing incident response processes, as well as the lack of effective endpoint and network monitoring solutions. Companies were caught on the back foot by an unprecedented situation and it has brought to the fore the lack of basic controls, and the lack of process to put it right, because many organisations have struggled for budget to sort this out in a meaningful way through the COVID crisis.”
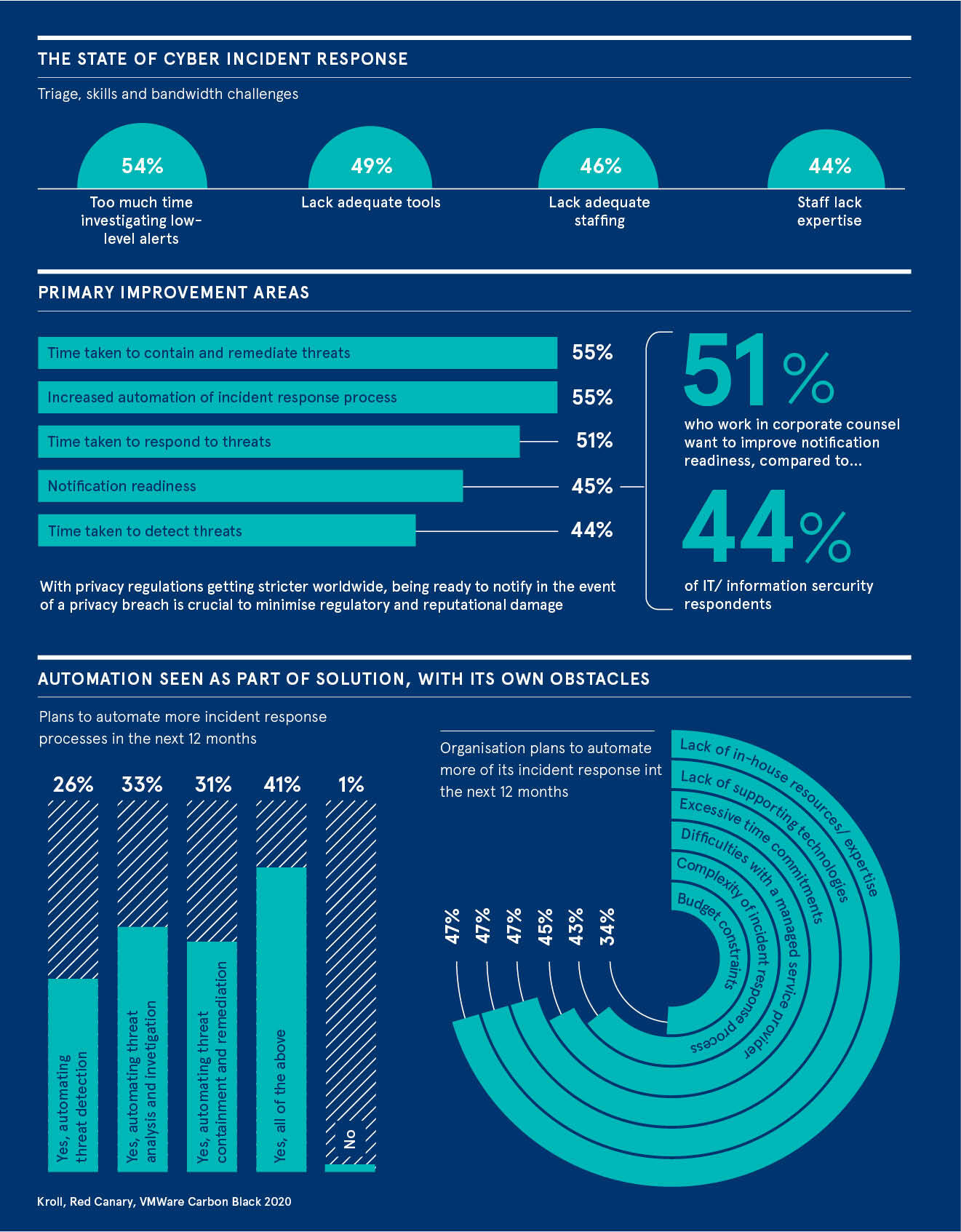
A recent study, conducted by Kroll, VMware Carbon Black and Red Canary among 500 security and legal leaders, found 93 per cent of large organisations have suffered at least one incident that led to a compromise of data over the past 12 months. And when a cyberattack occurs, 92 per cent said they are not completely confident in their ability to identify the root cause.
Security leaders indicate more security issues are likely, with two-thirds believing their organisation is vulnerable to a cyberattack that could disrupt business or lead to a data breach. Yet their ability to strengthen security faces numerous internal headwinds. Nearly half of respondents said they are not conducting regular security readiness exercises with leadership and that security is actually viewed as a business impediment.
The research also exposed some discrepancies between infosec teams and corporate counsel, with 52 per cent of the latter saying their organisation lacks readiness to notify in the event of a security breach, compared with 43 per cent of the respondents overall.
“It was not really a surprise to us that 54 per cent of security leaders said their organisation was spending too much time investigating the little incidents and couldn’t deal with the big ones,” notes Beckett. “What is interesting is seeing the different areas security staff and general counsel worry about. Corporate counsel worries about attribution: who was behind the attack? But much fewer people in security share that concern as they know the difficulties and costs involved in identifying perpetuators.
The attacker has to get lucky once, we have to be right 100 per cent of the time
“It is also interesting to see contrasting views on what is in place already. Over half of corporate counsel were fairly satisfied they had the right to audit their third-party vendors. Yet fewer than 40 per cent of security leaders thought it was in place or felt they had the right to check compliance and security standards being applied by third parties.”
Crucially, 55 per cent of organisations said they need to improve the time taken to contain and remediate threats, with the same number wanting to increase automation of the incident response process, yet half lack in-house expertise or technology to do so.
To support this growing need, Kroll has moved from managed detection and response to enhanced detection and response, and now to next-generation detection and response. Applying enhanced learning to the tooling deployed improves and accelerates the detection of indicators of compromise (IOCs) and the ability to link two or more areas that have been detected on the system quickly builds the bigger picture.
“The ability to quickly detect and then isolate an attack as a way of then getting it off your system is the biggest thing companies are working on at the moment to minimise business interruption,” says Beckett. “Our Kroll Responder service deploys endpoint agents to monitor networks and the endpoint. You quickly spot those IOCs or abnormal activities. We then have a team of shift-working analysts working 24/7 to detect those suspicious activities and do the initial triage, backed up by our global team of incident investigation and triage practitioners who analyse and determine what is going on.”
Three quarters of organisations already use third parties as part of their incident response process, according to Kroll’s study, and it’s clear partners will play a key role in providing the economies of scale required for effective monitoring and response. “Third-party partners facilitate the speed and the augmentation of in-house services that companies need, while dedicated monitoring technology gives the second and third-line support expertise to respond around the clock when a major cyberattack takes place,” says Beckett.
“The attacker has to get lucky once, we have to be right 100 per cent of the time. There is an arms race in terms of the exploitation of new technology between the attackers and defenders. Attackers are using enhanced learning, artificial intelligence and quantum computing to either generate the next-level attack or bypass security. On the defenders’ side, we have to quickly identify those tools and techniques in use. We are looking for the zero-day vulnerabilities to identify and patch them before the attacker develops an exploit. Use of our own enhanced learning and artificial intelligence helps us to do that.”
For more information please visit kroll.com/cyber
In 2015, Adrian Leppard, then City of London police commissioner, made a striking statement: cybercrime had eclipsed the drugs trade in value to organised crime and the police did not have enough resources to tackle it. It’s not often a police commissioner’s comments make it into the business pages of newspapers, but it was clear organisations of all sizes shared his concerns and, unlike with the drugs trade, they were all potential targets.
Since then, the proliferation of organised crime and get-rich-quick merchants on the internet has accelerated even further, amplified by a global pandemic that has seen fraudsters prying on people working from home. According to Kroll, the corporate investigations and risk consulting firm, national lockdowns have caused ransomware to overtake business email compromise as the principal attack affecting companies.
“Part of this is because there is no business as usual and it is huge money that can be made relatively easily without fear of detection or being caught,” says Andrew Beckett, managing director and Europe, Middle East and Africa leader for Kroll's cyber risk practice. ”IT estates are now distributed and it's harder to monitor for companies that didn't have strong monitoring in place beforehand. A lot of organisations are using out-of-date, unpatched VPNs and you’re not sitting next to a colleague who can just do a quick sanity check for you. ‘Does this look right to you?’ ‘Do you think I should do this?’ You don't have that option anymore.


