The question of data security is one that has rightly gathered pace in recent years. The emergence of the cloud has reshaped the digital landscape, offering organisations greater flexibility and efficiency, and transforming how businesses store and share data on an unprecedented scale, empowering even the smallest of enterprises.
But with it security has become something of a moving target and the risk of data breaches has risen dramatically.
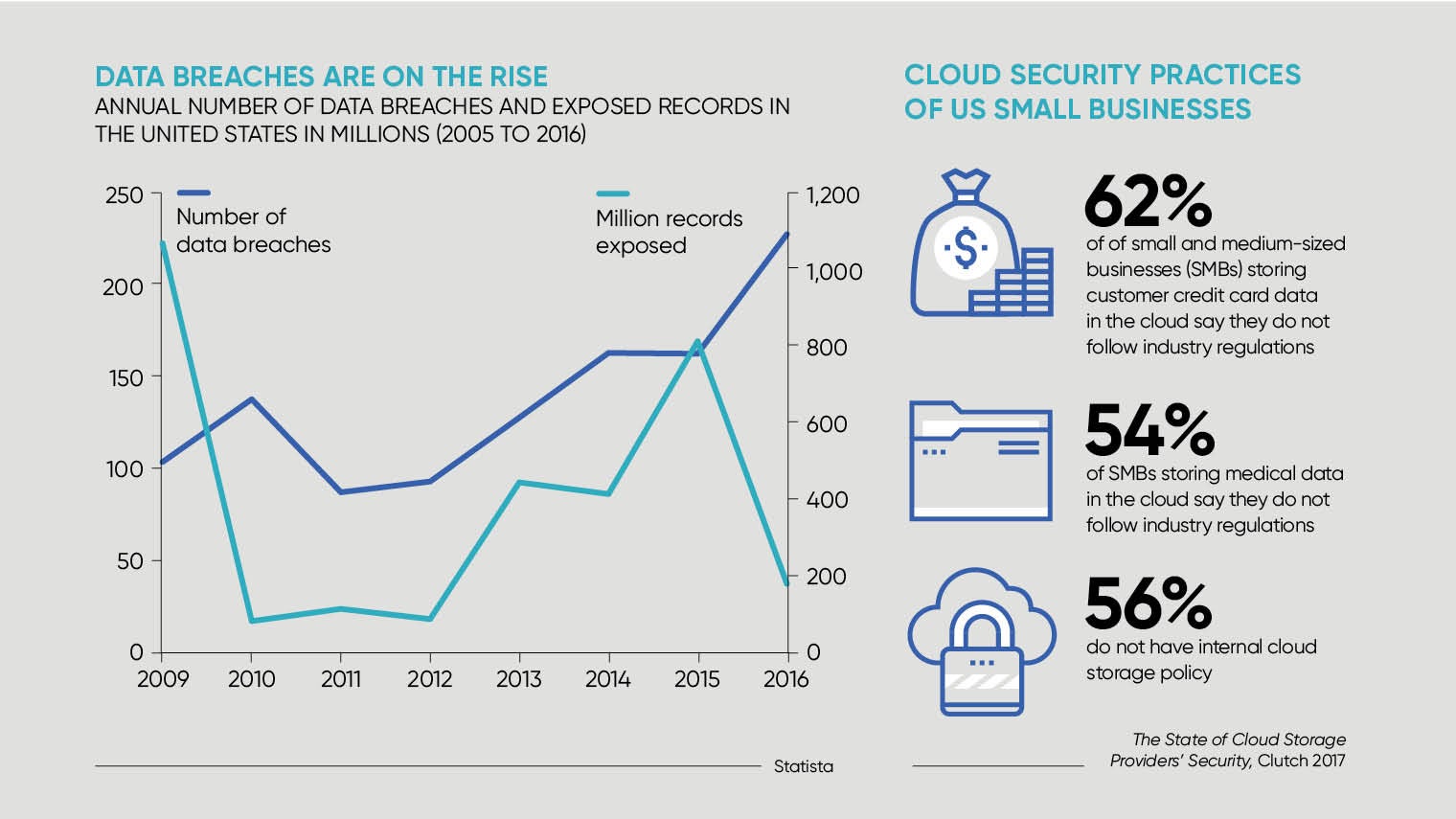
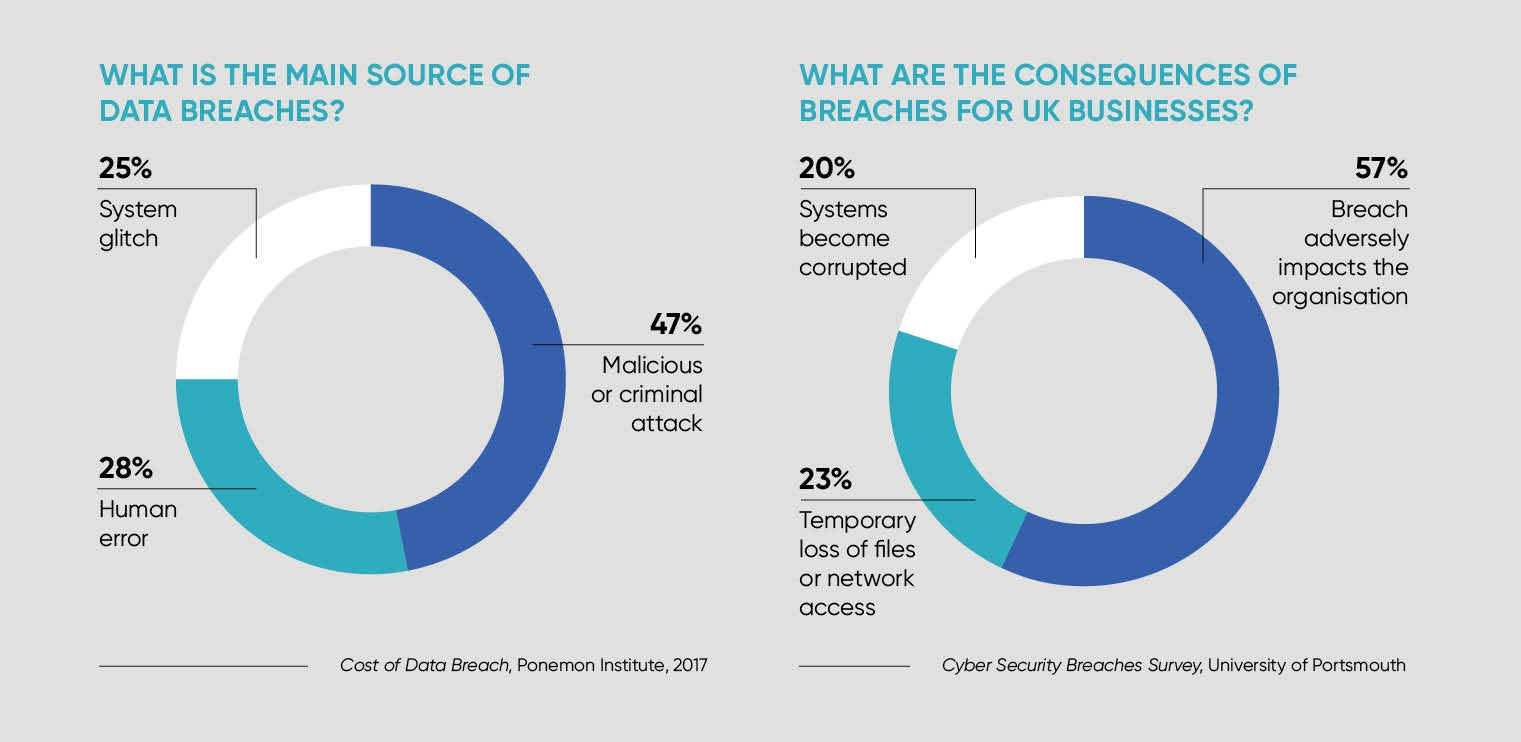
Government figures show that three fifths of businesses (61 per cent) hold personal data on their customers electronically and just under half (46 per cent) of all UK businesses fell victim to a digital attack during the last 12 months.
These numbers make for sobering reading and, according to cloud storage service Tresorit, businesses must act to fortify their defences.
“Increasingly businesses are storing confidential information online and, in an era of hacks that expose the data of millions of users, organisations simply cannot afford to take risks with their security,” explains Istvan Lam, chief executive and co-founder of Tresorit, the end-to-end encrypted file sync and sharing service for businesses. “Data has become a valuable currency, so protecting it should be a key priority for businesses.”
As technology advances at an unfathomable pace and organisations increasingly depend upon technologies beyond the traditional remit of their enterprise, many older precautions have become futile in the fight against breaches. For Mr Lam, the answer lies in end-to-end encryption.
Files are encrypted before they get sent to the cloud and are only accessible for the recipients and those you explicitly authorise
The notion of encryption is nothing new; cryptography can trace its roots back to ancient times. Its newest application, however, is revolutionising digital security.
End-to-end encryption provides a further layer of protection, ensuring encryption keys stay on the end-user’s device and thus only the sender and receiver can unlock the messages. As opposed to the in-transit and at-rest encryption used by the majority of providers, this approach means communications remain fully private.
“In the wrong hands, data can do more damage than you might realise,” says Mr Lam. “When you use the cloud, you leave yourself open to that service provider looking at the data or passing that access on to anyone they want. Tresorit is different; files are encrypted before they get sent to the cloud and are only accessible for the recipients and those you explicitly authorise. This means that your data cannot be read by others, including Tresorit.”
Additionally, Tresorit has a dashboard for IT admins to further help businesses maintain control over how team members share files.
But the importance of end-to-end encryption is not simply limited to helping businesses bolster their security capabilities; encryption will play a key role in meeting tougher regulatory requirements.
In May, the General Data Protection Regulation (GDPR), designed to unify data protection in all European Union countries, will come into force and it’s set to be a game-changer for the way in which businesses use and share personal data.
Organisations will need to ensure personal data is managed in a safe and secure manner, has been gathered lawfully, and will only be used for the purposes for which it was intended. Those who fail to comply face heavy fines of up to 4 per cent of global turnover.
Mr Lam says: “Cloud-based applications are useful, but they could create risks for business data. Under the GDPR, organisations are responsible for protecting all personal data throughout its life cycle, from collecting to processing it with third parties such as cloud-based services. The changes are particularly pertinent for smaller businesses that may not have the resources of their larger counterparts. As such, deploying simple yet highly effective technology is a vital step in becoming compliant.”
In the event of a server-side data breach, encryption and especially end-to-end encryption makes the leaked data unreadable for the hackers. They will only get hold of the encrypted dataset which is like white noise. Not only does encryption have the advantage of helping businesses better protect data, but it makes the compliance process easier and reduces associated costs.
Mr Lam adds: “Meeting GDPR compliance requirements will not be easy for businesses. However, we should not only think of this as a compliance process, but an opportunity to improve the trust of consumers in digital services, and to take steps towards protecting the personal data of staff and customers.”
For more information please visit www.tresorit.co.uk
TRESORIT TRANSFORMS STORAGE FOR LITTLE VENICE PARTNERS
After experiencing an accidental information leak with Dropbox, financial advisory firm Little Venice Partners (LVP) was in need of a secure cloud-storage solution. The solution needed to function as a virtual dataroom during transactions, providing seamless and secure sharing and ease of use.
When a firm’s involvement in a project ended, LVP also needed to ensure access to sensitive files was revoked. After unsuccessfully trying a number of products, LVP discovered Tresorit and has not looked back.
Robert Frodsham, LVP associate, says: “After a partner’s Dropbox account was compromised, switching to Tresorit couldn’t have been simpler for us. Their customer service is some of the best I’ve ever experienced.”
Since switching to Tresorit, LVP hasn’t experienced any threat to its data and is able to work with clients confident that its data is shared and stored securely.
TRESORIT RESULTS IN SAFER BUSINESS AND COMPETITIVE EDGE FOR ALPHA INDEPENDENT MORTGAGES
Dealing with sensitive information on a daily basis, insurance and mortgage provider Alpha Independent Mortgages needed a solution that was simple for clients to use, but secure enough to protect the business.
Guy Applebee, partner at Alpha Independent Mortgages, explains: “Clients were frustrated with encrypted email and often sent sensitive documents in plain email. Sharing with Tresorit is easy. People appreciate that we handle their documents securely. It sets us apart from our competitors.”
Since switching to Tresorit in 2013, Mr Applebee noticed an immediate, drastic decrease in the number of complaints and frustrated customers. As a result, the company spends less time giving technical support, while providing more security for its clients. What’s more, using Tresorit has proved a selling point to new clients, with the promise of user-friendly security throughout their communications.