Rapid advancements in technology in recent years have given businesses far greater mobility, accessibility and interconnectivity. Though this has provided enormous value, it has also meant more users have the capability to commit harmful behaviour, fraudulent or otherwise. The growing popularity of remote working has compounded this risk further by enabling users to commit malicious activity from wherever they are in the world.
Organisations are no longer just bricks and mortar. Contracting and outsourcing are also on the rise as companies are trying to keep pace in a more competitive space, leading to less human oversight and an environment where insider fraud can become more prevalent and difficult to detect. Assets come and go every day, meaning they can no longer rely on perimeter security. They need complete visibility both on and off the corporate network.
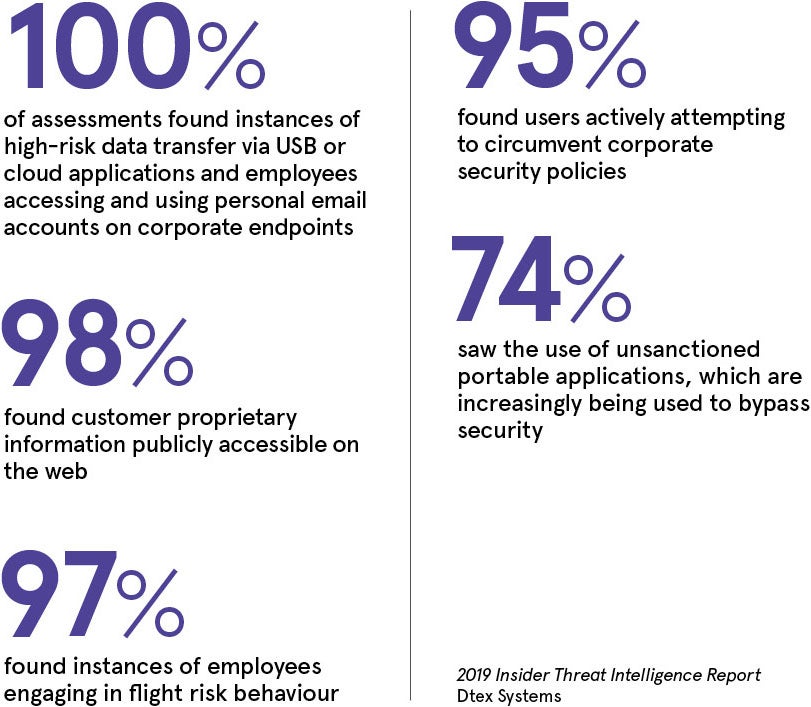
The 2019 Insider Threat Intelligence Report, which collects data from Dtex Systems’ risk assessment findings over the previous year, found some form of undetected insider threat in every assessment, including high-risk data transfers via USB or cloud and employees using personal webmail. Users were found to be bypassing security in 95 per cent of assessments and in 98 per cent of assessments Dtex found proprietary company data that was publicly accessible on the web.
According to the 2018 Cost of Insider Threats Report, insider threats cost businesses an average of $8 million an incident. Yet until a few years ago, users accessing data within an organisation almost entirely evaded the attention of security teams. Today insider fraud is increasingly prevalent and companies struggle to even detect it in the first place.
“All businesses, no matter the industry, are at risk of malicious insiders,” says Armaan Mahbod, manager of insider threat and cybersecurity investigation at Dtex Systems. “These malicious actors can come from any role, not just pre-determined groups of ‘high-risk’ job titles. Therefore, a continuous audit trail of all users, devices and applications within an organisation is critical to catch warning signs and conduct effective investigations.
“Organisations are often too late and tracks have already been covered. In a recent phishing attack on an Australian university, for example, they didn’t have the audit trail to effectively investigate after the incident, which severely hampered their recovery and response.”
Companies typically have some form of fraud controls in place, including thresholds and limits, to identify specific transactions. However, many offenders are high-level executives, managers or otherwise, who are fully aware of the limits and go below the thresholds to avoid detection from suspect transactions. They may steal smaller quantities of data or money over a long period, resulting in the largest cumulative value stolen.
Organisations cannot defend against attacks that they cannot see… With greater visibility comes greater certainty, which translates to more efficient investigations
Most commonly, the individuals that are committing malicious insider activity are people in positions of trust, who already have some level of authorised access to critical systems. This is why it is so important to understand the insider threat kill chain, says Mr Mahbod.
“Methods for intrusion and exfiltration are constantly evolving, but it is nearly universal that malicious insiders will attempt to cover their tracks, or circumvent security tools or alerting thresholds,” he adds. “We consistently find that investment in detecting these early stages of the kill chain, like covering tracks or security bypass, gives organisations the best return and results. Just as one example, Dtex caught data theft by a foreign national at one of our customers, AMP, due to the culprit’s attempts to circumvent company security.”
There are two factors that make insiders a greater fraud threat than outside attackers. Their malicious attacks are not premeditated and they rarely act immediately after being brought into an organisation. Instead, they slowly accumulate insights on all the traps set in place. Secondly, inside attackers generally have some level of authorised access, either in their current role or a previous role within the same company.
Malicious insiders, who are responsible for 22 per cent of all insider threats, primarily use permitted applications to evade detection, including uploading data to online file-sharing sites sanctioned for business use, utilising personal webmail accounts that aren’t monitored and unblocked data-dumping websites.
In Dtex’s report, 95 per cent of assessments also identified employees using anonymous and private browsing, which was an increase from 60 per cent the year before. When there is no malicious intent, threats can be even more difficult to detect, as is the case with the 68 per cent of insider threats that are purely down to negligent users causing accidental harm. This makes the visibility of user behaviour across the entire organisation crucial.
“Organisations cannot defend against attacks that they cannot see,” says Mr Mahbod. “Also, placing monitors on critical systems is not enough because it only gives you less than half the full story. When a malicious insider steals data from a critical system, transferring the data to their own device, what did they do next? With greater visibility comes greater certainty, which translates to more efficient investigations.
“On the flip side, when you don’t have visibility across an organisation and look at a specific device or IP address for security incidents, you run the risk of creating too many false positives because your solution does not have all the organisational domain context it needs to determine whether an activity is high risk. You need historical activity of the user, a comparison to their peers and the organisation to make a stronger determination.”
Dtex Systems provides the comprehensive end-point visibility that companies need at scale to understand, in near real time, any abnormal user behaviours which have led to identification of fraudulent behaviour. Furthermore, Dtex’s data highlights the contextual information necessary to understand the bigger picture behind users’ malicious actions.
“Through this visibility and the elevation of anomalous behaviour, Dtex enables organisations to be ‘left of boom’, which means the organisation is building and running a security posture that gets out in front of the threat, allowing security teams to act before an incident, not just respond after the fact,” says Mr Mahbod. “By seeing the full kill chain of events, companies are able to identify suspicious behaviour prior to events actually harming the business. This allows organisations to be proactive rather than reactive.”
For more information please visit dtexsystems.com




