Growth of the internet in the 1990s fuelled an era of globalisation defined by a rapid pace of innovation, open trading and cross-pollination of technology across borders. However, populist movements in recent years have sought to reverse this tide and return to more protectionist postures. Fracturing trust among world leaders last year resulted in a rising number of trade sanctions and embargoes between nation states.
These trade disputes restrict nation states from acquiring technologies and intellectual property (IP) vital to their local industries and security, while enterprises in affected countries also risk losing access to new innovation and information.
The result is the emergence of a cyber cold war reminiscent of the late-1940s to early-1990s when nation states frequently acquired technologies and IP via espionage. But rather than sending in spies to physically steal information, the difference this time is the theft will be carried out
through targeted data breaches launched remotely.
It’s not only governments and security agencies that should be worried about these attacks because businesses are likely to be caught in the cyber-crossfire, according to Luke Somerville, head of special investigations at Forcepoint Security Labs.
“It’s often IP supplied to governments by private organisations that other nation states want to get their hands on, such as the designs for components, which may make their way into critical tools and infrastructure,” he says. “If they’re no longer able to access that expertise on the open market, they will target those companies with a high calibre of cyber-attack to steal them instead.
The answer lies in understanding the points at which people and data interact
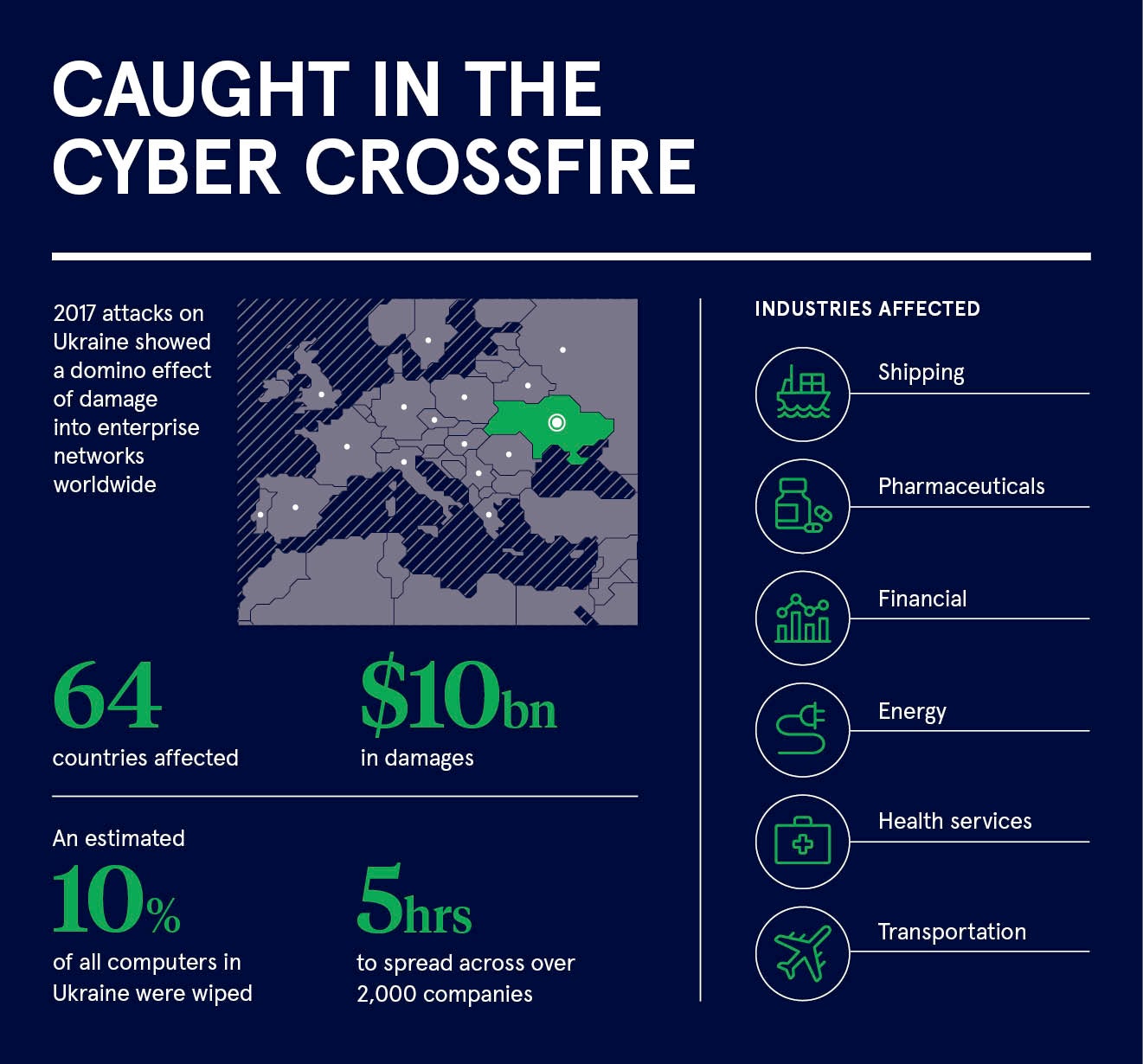
“Even if your company has no direct link with a target, you could still be affected. Beyond the general risk of collateral damage – the malware used on the 2017 cyber-attacks on Ukraine, for example, spread globally – you may be a target if you supply a government supplier or are even further down the chain. Compromising your systems may make it easier for the attack to flow up the supply chain and reach the real target.”
The cyber cold war means enterprises must ensure they have the right security in place to protect themselves from these kinds of cyber-attacks and prevent theft of their IP. Businesses certainly can’t be accused of not trying to do this as worldwide spending on information security products and services will exceed $124 billion this year, according to Gartner, but established approaches appear to be failing.
The number of vulnerabilities, data records, new malware samples and malicious programs continue to grow each year, and large-scale data breaches are covered in the media on a regular basis. Executives are kept awake at night worrying about the impact a cyber-attack could have on their business and are well within their rights to ask why the extensive funding they’re putting into security is not providing the protection
they need?
“The current paradigm is broken,” says Duncan Brown, chief security strategist, Europe, Middle East and Africa, at Forcepoint. “There are tonnes of technology deployed out there, which is effective to a degree, but not stopping the breaches. The paradigm is to constantly try to second guess the hackers, essentially by looking in the rear-view mirror, but it’s a fool’s game.
“The attack community is much more creative than that. The paradigm needs to change. We can’t keep spending all this money where it is palpably not working. Broadly, there are two main ways to prevent theft of your critical data: hope and pray, or get on the front foot and organise yourself to expect an attack. Many are still in the former mindset.”

Forcepoint, a cybersecurity software provider, advises all companies to expect to be breached and to plan accordingly with a full incident response plan in place. Often the worse damage comes not from the attack itself, but the way the organisation responds. Equifax and TalkTalk both suffered significant damage to their brands by responding to their respective data breaches in a poor and knee-jerk manner.
In the world of cybersecurity, knowledge sharing is also crucial. While many organisations tend to prefer to isolate themselves and keep intelligence in-house, this can restrict the overall ability of businesses to prepare effectively. A competitor to your products and services is still an ally in a cyber cold war and should be seen that way.
Most of all, however, companies must now be prepared to switch their whole approach to security, focusing on understanding where their valuable assets are rather than on a physical perimeter or stopping attacks from getting in.
“The technology keeps being superseded by new threats,” says Mr Brown. “When a new threat vector is revealed, everybody scrambles around trying to fix it. We’ll never have a 100 per cent view on the threat landscape, so we need to flip the paradigm and focus on what we can control.”
The answer lies in understanding the points at which people and data interact. Human interactions with data underpin every organisation, so tracking and analysing those interactions in detail enables companies to understand what’s abnormal. Once they know what’s abnormal, they can quickly and accurately detect when something is wrong.
Forcepoint calls this approach human-centric behaviour analytics. Downloading a certain file may be normal for one employee, but abnormal for another. Understanding that context enables organisations to know what it is in control of and, by establishing a base line, determine what is safe from what is unsafe. It puts them on the front foot.
“We’re trying to orientate the security strategy in an organisation around behaviour of people and their interaction with critical data, then use the technology to provide the telemetry that informs the model,” says Mr Brown. “By understanding what the normal behaviour pattern is you can apply different risk assessment to each user.
“Lots of companies really can’t predict how they’re going to be attacked, but they worry about it a lot and this vulnerability stops business from doing what needs to be done. By understanding user behaviour and the key data assets, you can free up that business. Human-centric behaviour analytics is the core engine that gathers the telemetry, and by gathering all of the telemetry from our various security systems, we can get a very accurate sense of how users are behaving on a network and interacting with data.
For more information please visit www.forcepoint.com





