 Your biannual Cybercrime Report is always highly anticipated due to the volume of transactions you process. What trends caught your eye in the latest report?
Your biannual Cybercrime Report is always highly anticipated due to the volume of transactions you process. What trends caught your eye in the latest report?
We process more than 35 billion online transactions a year globally so that gives us a really interesting perspective on what’s going on in the world of cybercrime. Our latest report, which covers the period between July and December 2019, shows quite a significant tipping point in terms of the platforms that fraudsters target. Four years ago, mobile devices made up about 20 per cent of our network traffic. In the latest report, it’s about two-thirds. The shifting consumer behaviour from desktop to mobile has clearly been happening for a long time, but there were always more attacks on desktops than on mobile. That’s partly because the volume was slowly shifting, but also partly because fraudsters traditionally saw desktop transactions as an easier target because mobile transactions are set within the often more secure framework of a mobile app, with the likes of fingerprint biometrics, for example. In the last six months of 2019, however, mobile attacks outpaced desktop attacks by volume for the first time.
Mobile usage has exceeded desktop for some time now. Why is it only just recently that fraudsters have decided to target this platform more than desktop?
One of the reasons it happened in this period is because we did see a big growth of global bot attacks primarily targeting mobile app registrations, so it might be that in the first six months of 2020 we see those attack volumes edge back towards desktop again. However, a mobile bot attack, in itself, indicates a clear shift in fraudsters’ approach. We’ve seen big, automated bot attacks in the network consistently over the last few years and the fact that fraudsters are now using bots to target mobile applications indicates a change in their behaviour.
What does this mean for organisations and how they approach cybersecurity?
Any one individual solution can eventually be broken by fraudsters, but layering up multiple tools together is a really good way to protect organisations and their customers. Most organisations have been thinking about mobile security for a number of years now, but there are some evolving technologies that are really interesting, particularly in the context of regulation. One of the most innovative emerging technologies at the moment is behavioural biometrics. That doesn’t refer to fingerprint or iris scanning, but rather identifying high-risk behaviour from the way users interact with their devices. On mobile, this could mean the way they swipe, hold their phone or touch their screen. All these pieces of information can be combined to understand and identify risk, and be used in the future as one component of a strong customer authentication workflow to support the second European Union Payment Services Directive (PSD2).
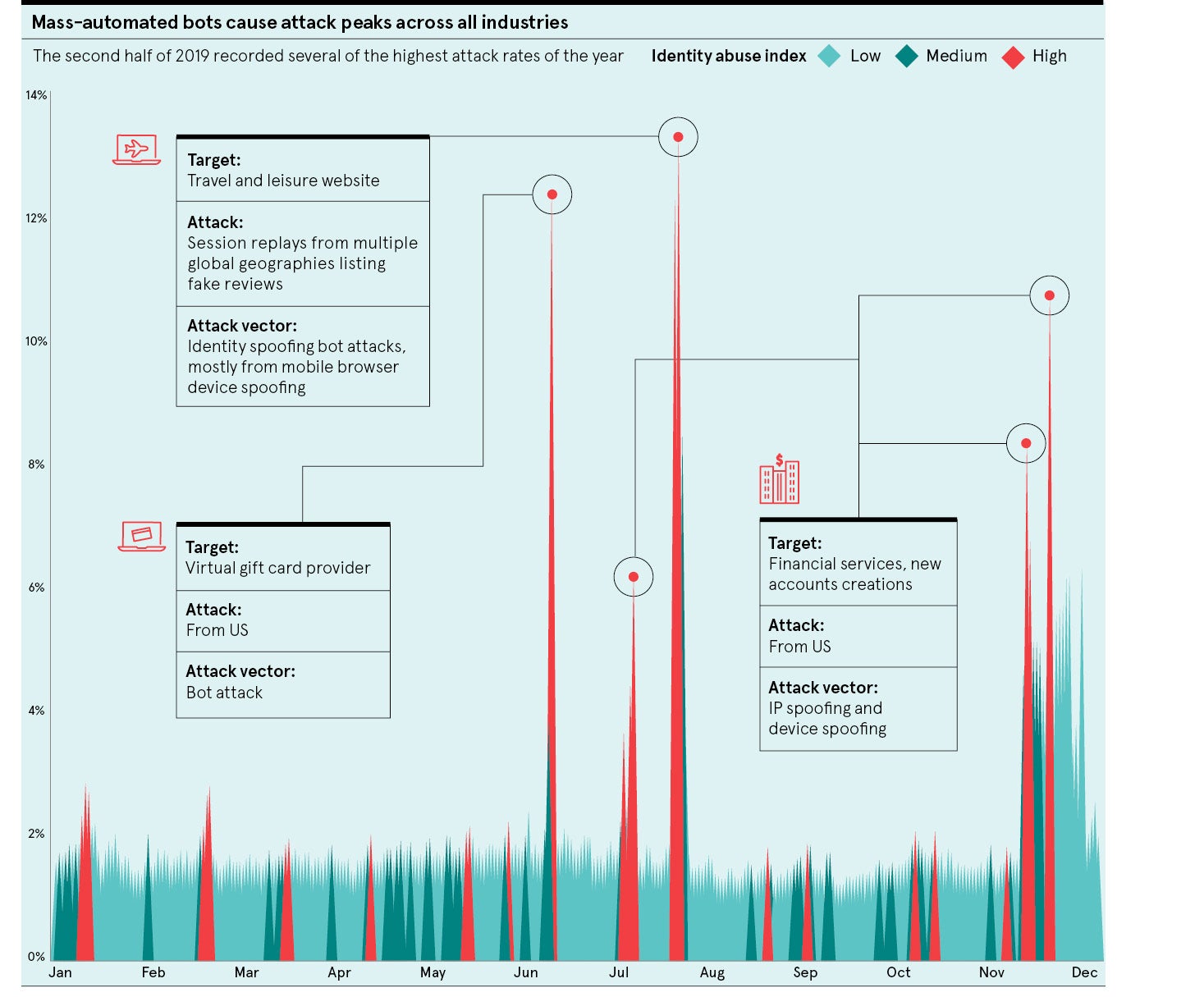
What have you been able to learn about the way fraudsters operate?
Last year we started tracking individual fraudsters using their digital identity and we found they were operating across multiple organisations within our network. In our latest report, we took our analysis a step further by visualising the pattern of when a device that had been associated with a confirmed fraud event at one organisation had then been seen at another organisation. By connecting these events, we were able to see this huge network of interlinking fraudulent activity. We broke those networks down into specific smaller networks that we see operating across particular regions or industries. The global network we mapped out had around 73,000 devices that were associated with a fraudulent event at one organisation and then recorded at another. During just a one-month period, those transactions amounted to more than $40 million of monetary exposure to this network of cross-organisational fraud. It feels like if they can work in that kind of advanced and interconnected way globally, they must have a very advanced set-up and process. This networked concept of fraud was a real eye opener.
How is LexisNexis Risk Solutions helping companies deal with this network of fraudsters?
It takes a network to fight a network and so we are building that through what we call the LexisNexis® Digital Identity Network®, which is a crowdsourced repository of digital identity intelligence harnessed from these billions of global transactions. With each transaction we can look at numerous pieces of information, such as the device integrity, location data, user behaviour and whether there is any threat intelligence associated with the online transaction. From all these insights we are able to build a digital identity for each user and our technology can then flag if any activity seems inconsistent or unusual. 
We are using all of the individual components of someone’s digital identity, stitching them together and using that as a baseline to analyse and understand whether transactions are high risk or trusted. On top of that there are many other components we layer in for additional security. We have numerous physical identity solutions that customers can use, either in know-your-customer, or KYC, requirements or to verify the physical identity of a user, as well as a decision platform, which incorporates machine-learning tools and advanced behavioural analytics to better model fraud risk. We’re then developing new and innovative solutions such as behavioural biometrics, which we recently launched, to layer in additional data about how users interact with their devices.
This holistic solution allows us to detect the macro attacks, like automated bots, as well as the individual attacks on customer accounts, and even social engineering attempts. A key challenge for financial institutions at the moment is fraudsters targeting customers by calling them, impersonating the bank, playing on their fears by saying their account has been hacked and then gaining remote access to steal from them. Our system can help organisations detect if this is happening and help them block high-risk behaviour before it jeopardises good user accounts. The ability to compare the physical identity of a user with the digital identity and behavioural information provides a layered solution to protect organisations and their customers.
How do you foresee the cyber-threat landscape continuing to evolve in the coming years?
We will continue to see this macro to micro trend where attacks are happening on a mass scale, but also an individual scale. That means more mass-scale, global attacks happening across country borders and industries as fraudsters look to maximise their success. In addition, we are likely to see more social engineering attacks, a popular tactic with cybercriminals who often target vulnerable people less likely to detect what is occurring. Being able to identify attacks across this very broad spectrum is important. Fraudsters will always look for the lowest common denominator to attack and generally the customer will be the weakest link in the chain, so it’s crucial organisations implement the solutions that really enable them to protect their end-users from the effects of fraud.
For more information please visit www.risk.lexisnexis.com/cybercrime-report



