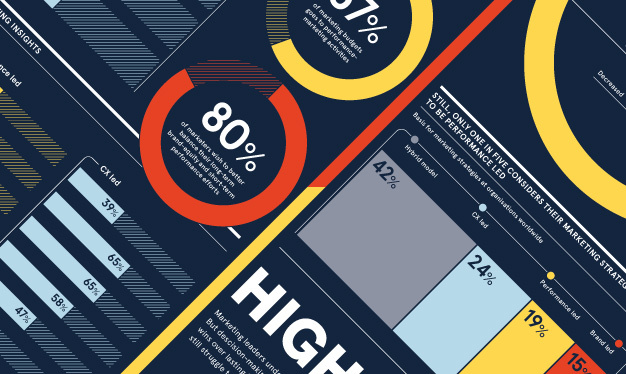
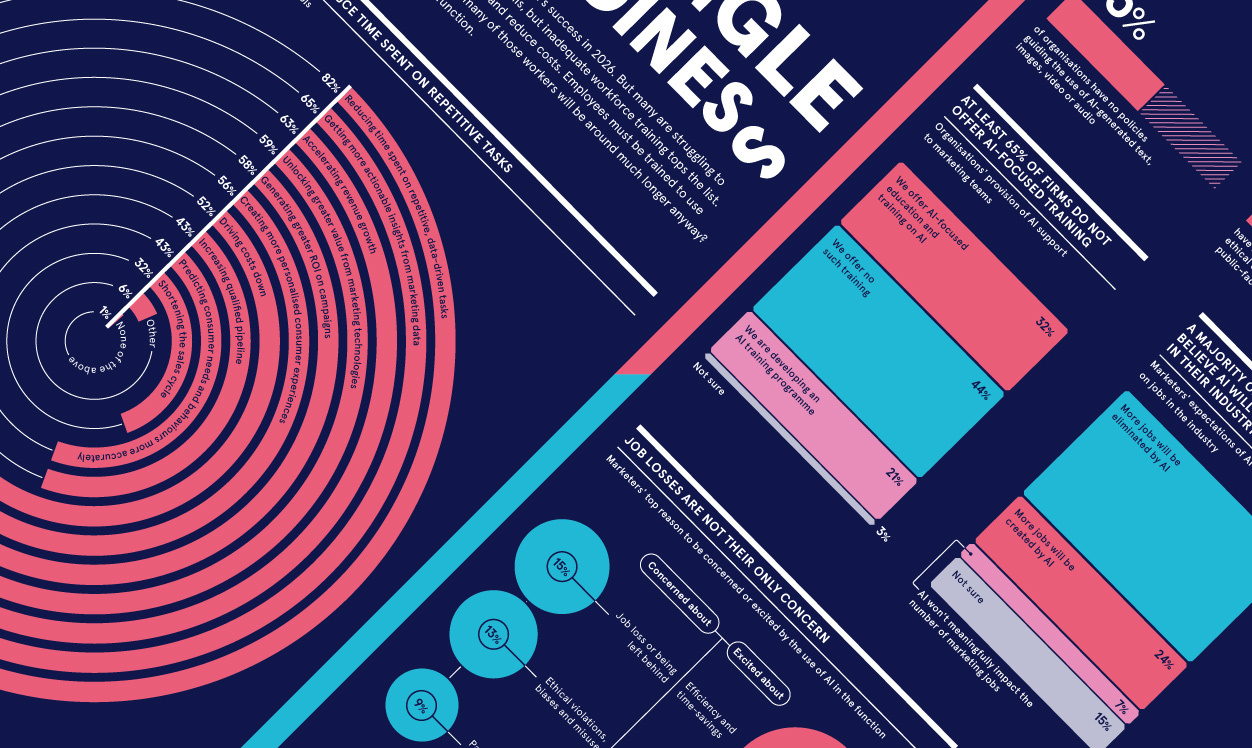
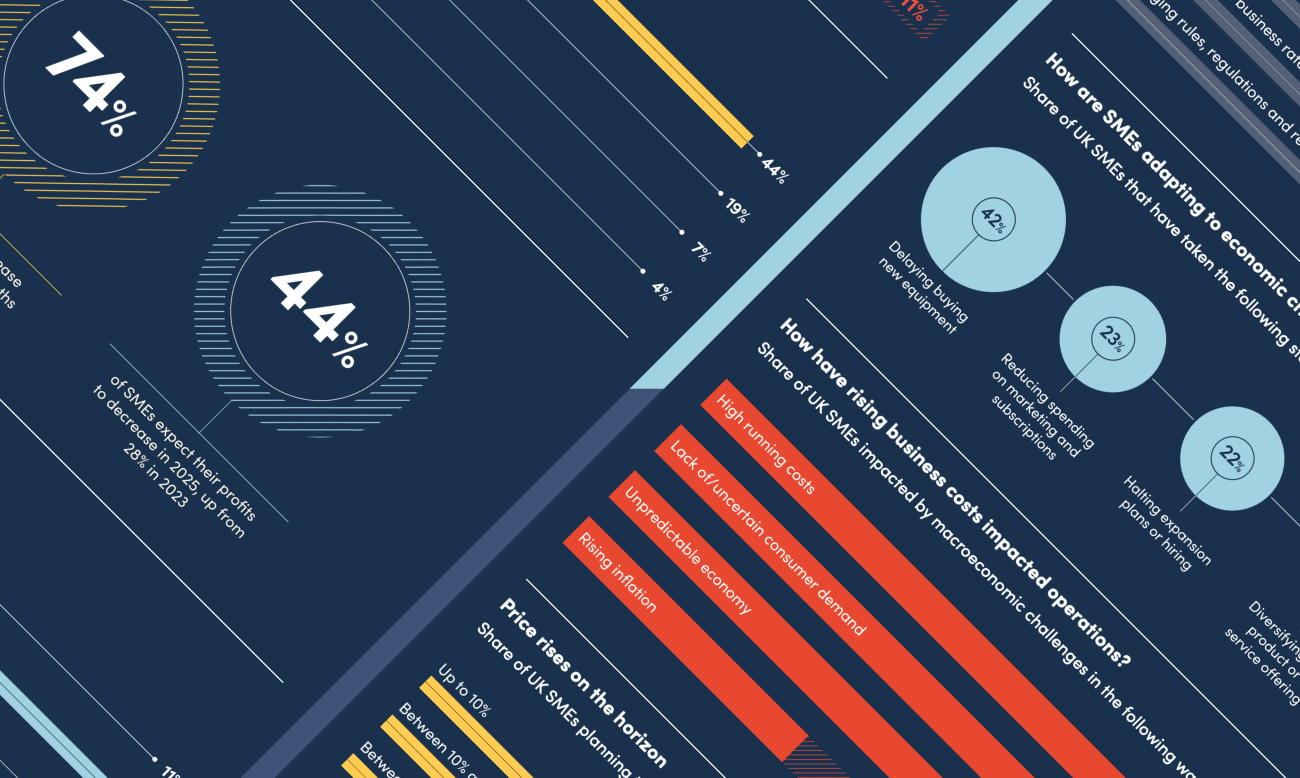
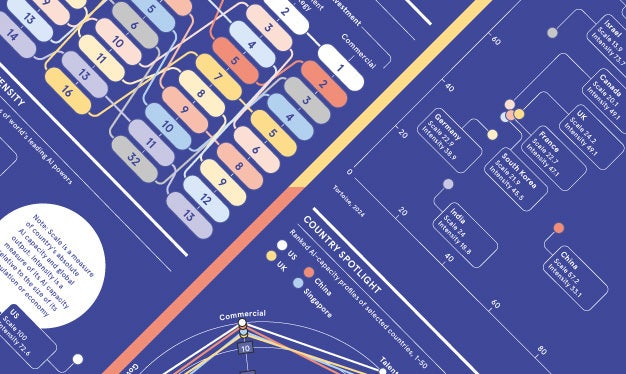
Unsurprisingly, usernames and passwords are the most common method of authentication when it comes to internal enterprise cybersecurity. But, according to IT professionals, they're not the most secure. This infographic explores the various ways companies are identifying employees and protecting the wider organisation, and how they are taking steps to improve cyber-resilience