“All we need is for one of us – just one, sooner or later – to have the thing we’re all hoping for… one… good… day.” Fans of the hit TV series Buffy the Vampire Slayer may recognise that – it’s the vampire Spike explaining to Buffy why her life expectancy is irredeemably short. It also serves as a metaphor for cyber attackers and IT systems – there are an untold number of them and one of you, and all they have to do is have one good day.
Protecting the industrial internet of things requires a mental shift from protecting enterprise IT. With enterprise IT, the biggest threat is typically to data that may be exfiltrated, deleted, rendered inaccessible – as in ransomware – or published. With industrial control systems, the threat shifts to physical damage.
“I don’t think these threats are over-hyped,” says Chris Hankin, the Imperial College London professor who leads the multi-university Research Institute for Trustworthy Industrial Control Systems.
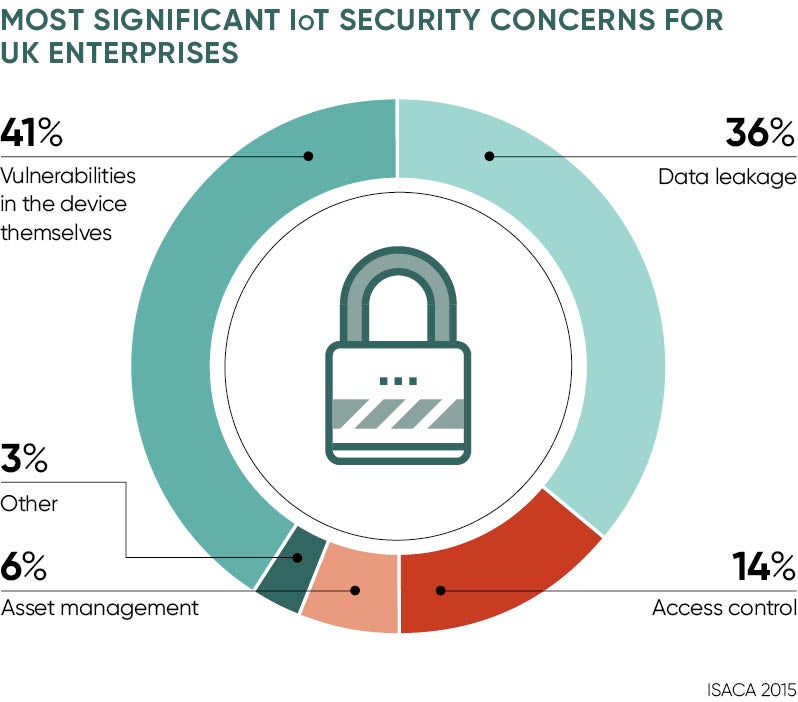
IoT attacks
He cites statistics from the US-based Industrial Control Systems Computer Emergency Response Team (ICS-CERT), which show a steadily increasing number of incidents over the last five years. Their 2015 report tallied 295 reported incidents and, while that’s a small number compared to today’s near-daily headlines about data breaches, the examples he cites are scary enough.
The earliest example dates from 2000 in Australia, when an attack on Maroochy Shire Council’s computerised waste management system caused millions of litres of raw sewage to spill into rivers, parks and hotel grounds. In 2015 and 2016 Charlie Miller and Chris Valasek showed they could use a Jeep Cherokee’s internet connection to immobilise it remotely on a highway, cause unintended acceleration, slam on the brakes and turn the steering wheel.
Professor Carsten Maple, of the University of Warwick’s Cyber Security Centre and the PETRAS Internet of Things Research Hub, adds a few more such tales. In 2014 the German Federal Office of Information revealed that an attack caused millions of pounds worth of damage by overheating the furnace in a German steel mill.
Last year a ransomware attack spread across the computers belonging to San Francisco’s municipal transportation system; rather than pay the $73,000 the attackers demanded, staff opened the gates and allowed passengers to ride for free for two days while they restored the system from backups.
It’s surprising how lax some very big manufacturers are about their products
Also last year a former employee used a virtual private network to breach Georgia-Pacific and reach one of its paper towel factories, costing an estimated $1.1 million in lost or spoiled production.
In both 2015 and 2016 attacks on substations turned off power to tens of thousands of Ukrainian households. And let’s not forget Stuxnet, which attacked computer controls over the centrifuges used to refine uranium within Iranian nuclear facilities, damaging them and the country’s nuclear programme. As harbingers of things to come, none of these is trivial.
“If you look at the ICS-CERT annual report,” says Professor Hankin, “the major sector experiencing cyber incidents until 2014 was energy. Then in 2015 the largest was critical manufacturing, though energy was still quite big.”
Scott Lester, principal researcher at Context Information Security, comments: “From our experience, all traditional manufacturers are struggling to keep up.” The desire for speed to market is a key issue, but he adds: “It’s surprising how lax some very big manufacturers are about their products. People aren’t even thinking about existing threats.” And, as Spike said, it just takes one successful exploit.
A key element, says Professor Maple, is understanding that in terms of security it’s not helpful to think separately about operational technology, such as industrial control systems and enterprise IT. In many cases, such as the Jeep Cherokee, they may be linked because of poor design which failed to implement sandboxing to segment the driving system from the entertainment system. In others, changes over time may open up undocumented connections.
Professor Hankin agrees: “Almost all of the case studies we know about seem to have started off with some compromise of the enterprise IT system as a way of getting to the industrial control system.” The anatomy of the attack is a bit different when a hybrid cyber-physical system is involved and the goal is substantially different, but separating them is meaningless when the vector for infection for something as sophisticated as Stuxnet begins with a phishing e-mail.
The issue of safety
Safety adds complexity because one of the first things security people will tell you is to ensure that everything is patched and up to date. But, as Professor Hankin notes, changes to software should trigger a safety recheck, a much more expensive process and one companies do not typically expect to undertake with anything like the frequency of today’s software patching.
Worse, he adds, sometimes the two are in conflict. As a simple example, consider a tube station where something has gone wrong. Security might dictate closing the barriers and keeping people in, while safety might dictate opening the barriers to let them out.
None of this is to downplay the usefulness of the industrial internet of things in terms of improving efficiency, reducing waste and adding flexibility. What’s crucial is tobe aware of the security issues that come with adding communications capabilities to legacy systems.
When you put operational technology into the cloud or connect in any way to the internet you have a problem
This will be even truer as consumer-grade internet of things devices penetrate previously manual factory areas. Even if the systems themselves are air-gapped, workers in those areas may be wearing personal health monitors, smart watches or augmented reality headgear and, of course, everyone might be carrying a smartphone.
“When you put operational technology into the cloud or connect in any way to the internet you have a problem,” says Professor Maple. “You have to do a proper threat assessment. Does it give you benefit, are you aware of all the risks?”
Saverio Romeo, principal analyst at Beecham Research, recommends assuming the worst will happen, and developing strong remediation systems so you can recover quickly and safely. He also stresses the importance of designing in security from the beginning.
In response to the exploits Miller and Valasek, Fiat-Chrysler eventually recalled 1.4 million cars, which was surely more expensive than starting with a sandboxed design that separated the automotive control systems from the entertainment systems.
“Retrofitting is economically very expensive and difficult to do,” says Mr Romeo. “Design of a connected system requires proper security strategy, which includes the ability to remediate.” He recommends consulting the guidelines published by the European Cyber Security Group, Internet of Things Consortium and Industrial Internet Consortium. To that list Professor Hankin adds the National Institute of Standards and Technology and the UK’s National Centre for Cyber Security.
IoT attacks


